
Google Dorking, also known as Google Hacking, is a powerful technique that allows users to leverage advanced search operators to uncover hidden information on the internet.
Part 1: Google Dorking Fundamentals
Understanding Google Dorking
What is Google Dorking/Google Hacking?
Google Dorking refers to the practice of using advanced search operators in Google to find specific information that is not readily visible through standard searches. This method can reveal sensitive data such as login credentials, confidential documents, and even security vulnerabilities in web applications.
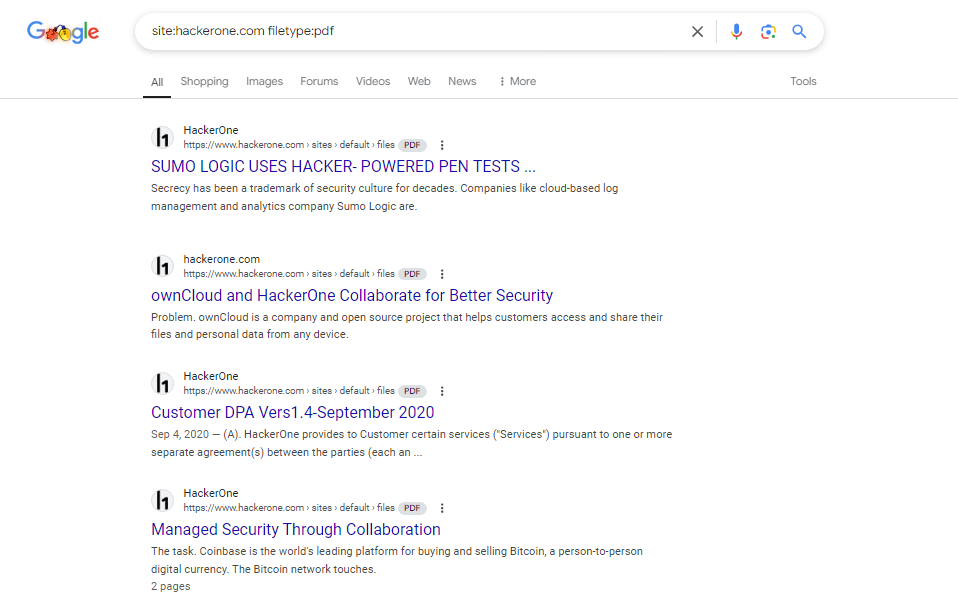
For example, a simple search like site:example.com filetype:pdf can yield all PDF documents hosted on the specified website. This capability makes Google Dorking a valuable tool for cybersecurity professionals, researchers, and anyone interested in gathering information from the web.
Mostly, Google dorking is used a s form of passive reconnaissance (information gathering) - an attempt to gain information about targeted computers and networks without actively engaging with the systems. This is ehy it is mostly considered legal, as no real damage is most of the information you already get is already available on the internet.

Here is an example of how google dorking is being used in the wild:
intitle:"index of" "back.sql" OR "backup.sql" OR "accounts.sql" OR "backups.sql" OR "clients.sql" OR "data.sql" OR "database.sql" OR "database.sqlite" OR "users.sql" OR "db.sql" OR "db.sqlite" OR "db_backup.sql" OR "dbase.sql" OR "dbdump.sql" OR "dump.sql" OR "mysql.sql" OR pic.twitter.com/CKwUloOpGn
— ./Mr-Dark (@Mr_Dark55) December 28, 2024
Legal Considerations and Ethical Boundaries
While Google Dorking can be an effective tool for research and security assessments, it is crucial to understand the legal implications. Accessing sensitive information without permission can lead to legal consequences. Ethical considerations should guide users in their approach, ensuring that they focus on legitimate research and security assessments rather than malicious activities.
Also, do not attempt to exploit the information gathered for malicious purposes. Doing so cal lead to legal consequences and this should only be done whenever explicit permission has been grnted.
Basic Search Operators
For a start, the basic search operators are essential tools for refining search results. Here the most some key operators:
site:This operator restricts search results to a specific domain or website. For instance,site:example.comwill only return results from that particular site.filetype:This operator filters results by file format. For example,filetype:pdfwill return only PDF documents.inurl:This operator searches for keywords within the URL of a webpage. For instance,inurl:loginwill return pages with "login" in their URL.intitle:This operator looks for keywords in the page title. For example,intitle:"confidential"will return pages with "confidential" in their title.intext:This operator targets keywords within the body text of a webpage. For instance,intext:"sensitive data"will return pages that contain this phrase in their content.
These operators can be combined to create more complex queries that yield specific results tailored to your needs.
Part 2: Advanced Techniques
Complex Query Construction
Complex query construction is vital for effective Google Dorking. You essentially achieve the complex queries by using Boolean operators and combining multiple search terms, users can refine their searches significantly.
Boolean Operators
Boolean operators allow you to combine or exclude keywords in your searches:
- AND: Ensures that both terms appear in the results (e.g.,
security AND vulnerabilities). - OR: Returns results containing either term (e.g.,
security OR privacy). - NOT: Excludes terms from the results (e.g.,
security NOT firewall).
Combining Multiple Operators
You can create intricate queries by combining different operators. For example:
site:example.com filetype:pdf AND intext:"financial report"
This query would return PDF documents from "example.com" that contain the phrase "financial report."
Using Wildcards and Special Characters
Wildcards (represented by an asterisk *) allow you to substitute unknown terms in your searches. For example:
intitle:"report * 2024"
This query would return pages with titles that include any word between "report" and "2024."
Additionally, using quotes (") around phrases ensures that Google searches for the exact phrase rather than individual words.
Specialized Searches
Specialized searches enable users to target specific types of information effectively:
Error Message Analysis: To find common error messages:
"404 Not Found"
This can reveal misconfigured sites or potential vulnerabilities.
Login Portal Identification: Use:
inurl:login
This targets login pages across websites.
Configuration File Exposure: To locate configuration files:
filetype:config
This can help identify misconfigured servers or applications.
Directory Listing Discovery: To find exposed directories:
intitle:"index of"
This query reveals directory listings where files may be publicly accessible.
Finding Sensitive Documents: Use queries like:
filetype:xls OR filetype:doc
This query helps locate potentially sensitive spreadsheets or documents across various sites.
The Google Hacking Database.
The Google Hacking Database (GHDB) is a comprehensive repository of search queries, known as "dorks," that leverage Google’s powerful search capabilities to identify security vulnerabilities and sensitive information across the web. The DHDB includes information relating to but not limited to the following:
- Vulnerable Files: Queries that can locate files containing sensitive data, such as passwords or configuration settings.
- Server Information: Dorks that reveal details about the server's software and version, which may be critical for exploiting known vulnerabilities.
- Online Devices: Searches that help identify devices connected to the internet, such as unsecured cameras or printers.
- Error Messages: Queries that expose overly verbose error messages which can disclose sensitive system information.
- Logon Portals: Searches designed to find login pages that may be vulnerable to brute-force attacks.
- Sensitive Directories: Dorks that reveal unprotected directories containing confidential files or backup data.
- And Much more

At the time of writing, the database contains over 7944 dorks which keep being added everyday.
Part 3: Security Applications
Defensive Google Dorking
Defensive Google Dorking involves using these techniques proactively to identify potential security issues within your organization or others.
Identifying Exposed Company Data
Regularly perform searches on your organization’s domain to identify any exposed sensitive data. For example:
site:yourcompany.com filetype:xls
This query can help you find any publicly accessible Excel files that may contain sensitive information.
Finding Security Misconfigurations
Search for common misconfigurations that could lead to vulnerabilities:
site:yourcompany.com intitle:"index of"
This can reveal directories that should not be publicly accessible.
Detecting Information Leaks
Leverage targeted searches to uncover leaked information:
site:yourcompany.com intext:"password"
This query helps identify any instances where passwords may have been inadvertently exposed online.
Vulnerability Assessment
Conduct assessments by searching for known vulnerabilities associated with specific software or services:
filetype:pdf "vulnerability report"
This can yield reports detailing vulnerabilities related to particular software versions.
Illustration of Defensive Applications
| Application | Example Query | Purpose |
|---|---|---|
| Exposed Company Data | site:yourcompany.com filetype:xls |
Identify sensitive Excel files on company domain |
| Security Misconfigurations | site:yourcompany.com intitle:"index of" |
Find exposed directories |
| Information Leaks | site:yourcompany.com intext:"password" |
Detect leaked passwords |
| Vulnerability Assessment | filetype:pdf "vulnerability report" |
Access reports on known vulnerabilities |
Information Gathering
Google Dorking is also beneficial for gathering intelligence about individuals or organizations:
Employee Information Discovery
Utilize LinkedIn dorks to gather employee names and titles:
site:linkedin.com "job title" "company name"
This helps build profiles of key personnel within an organization.
Infrastructure Mapping
Map out an organization's infrastructure by searching for publicly accessible services:
site:yourcompany.com
This reveals all indexed pages associated with the domain.
Technology Stack Identification
Identify technologies used by a company through targeted searches related to specific platforms or frameworks:
site:yourcompany.com "powered by WordPress"
This indicates if WordPress is being used as the CMS.
Digital Footprint Analysis
Assess an organization's online presence through various platforms and aggregate findings using comprehensive queries like:
site:*yourcompany* -www.yourcompany.com
This reveals all indexed mentions of the company across different domains except its main website.
Part 4: Best Practices
Safety and Risk Mitigation
To mitigate risks associated with Google Dorking, consider the following best practices:
Maintaining Anonymity
When conducting sensitive searches, use VPNs or proxies to maintain anonymity and protect your identity online.
Legal Compliance
Always ensure compliance with local laws regarding data access and privacy. Familiarize yourself with regulations such as GDPR or CCPA if applicable.
Documenting Findings
Keep detailed records of your findings for future reference or reporting purposes. Utilize spreadsheets or databases to organize information systematically.
Responsible Disclosure
If you discover vulnerabilities during your searches, follow ethical guidelines for disclosure. Contact relevant stakeholders privately before making any public announcements about potential security issues.
Building a Dork Database
Creating a personal database of effective dorks can streamline your research process significantly:
Creating Custom Queries
Develop tailored queries based on your specific needs and areas of interest. Experiment with different combinations of operators until you find what works best for you.
Organizing Search Strings
Categorize your dorks by type or purpose (e.g., sensitive documents, employee information) for easy access during research sessions.
Testing and Validation
Regularly test your dorks against current web content to ensure they remain effective over time. Adjust queries as necessary based on changes in web content or search engine algorithms.
Maintaining Effectiveness
Update your database as new techniques emerge or as existing ones become obsolete. Stay engaged with communities focused on OSINT and cybersecurity to learn about new developments in Google Dorking techniques.
Part 5: Advanced Applications
Automation and Tools
Automation can enhance the efficiency of Google Dorking significantly:
Custom Scripts for Google Dorking
Develop scripts using programming languages like Python to automate repetitive search tasks. For instance, you could create a script that runs multiple queries against different domains automatically and compiles the results into a single document.
Automated Query Tools
Utilize tools designed specifically for executing complex dork queries automatically. Some open-source tools allow users to input their dorks and receive structured outputs without manual intervention.
Result Parsing and Analysis
Implement scripts that parse search results into usable formats (e.g., CSV) for analysis or reporting purposes. Automating this process saves time and reduces human error when collating findings from multiple queries.
Integration with Other OSINT Tools
Combine Google Dorking with other OSINT tools such as Maltego or Recon-ng to enhance your investigative capabilities further. These integrations allow you to visualize relationships between entities discovered through dorking efforts effectively.
Future-Proofing
To stay relevant in the evolving landscape of online searches, consider these strategies:
Adapting to Search Engine Changes
Regularly update your knowledge regarding how search engines evolve their algorithms and indexing methods over time. Changes may affect how certain queries perform or what types of content are indexed prominently.
Emerging Search Techniques
Stay informed about new search techniques that may enhance your ability to gather information effectively (e.g., exploring alternative search engines).
Counter-Measures Awareness
Be aware of counter-measures employed by organizations against Google Dorking tactics; this knowledge helps you refine your approach when conducting investigations while avoiding detection or blocking attempts by target entities.
Staying Current with GHDB
Regularly consult the GHDB (Google Hacking Database) for new entries and techniques that may aid your research efforts; this resource is invaluable for discovering effective dorks used by others in similar fields of inquiry .

