
Last month, Apple announced a significant security upgrade to iMessage, likely the biggest since the app's creation. Dubbed PQ3 (post-quantum cryptographic protocol 3), this new encryption protocol will be used in Apple's default messaging application once users update their systems to iOS 17.4, macOS 14.4, or watchOS 10.4.
For those unfamiliar, quantum computers can run algorithms capable of breaking public-key cryptography schemes like RSA and ECDH (Elliptic Curve Diffie–Hellman) much faster than classical computers. While quantum computers are still in their infancy and quantum-resistant encryption is even newer, most software companies have yet to update their encryption protocols to address this emerging threat.
The threat posed by quantum computers breaking encryption is more imminent than some realize, especially regarding governments or corporations with the capability to archive large amounts of encrypted data flowing through the internet. The NSA, in particular, is currently storing messages, waiting for the time when they possess a quantum computer powerful enough to decrypt them.
Decoding PQ3
You might wonder what the "3" in PQ3 stands for. Contrary to assumptions, it doesn't indicate Apple's third iteration of post-quantum encryption. Instead, the "3" represents a "level three security" metric invented by Apple to measure the strength of encryption.
Apple's Encryption Level Chart
In Apple's encryption level chart, they unsurprisingly place themselves at the top:
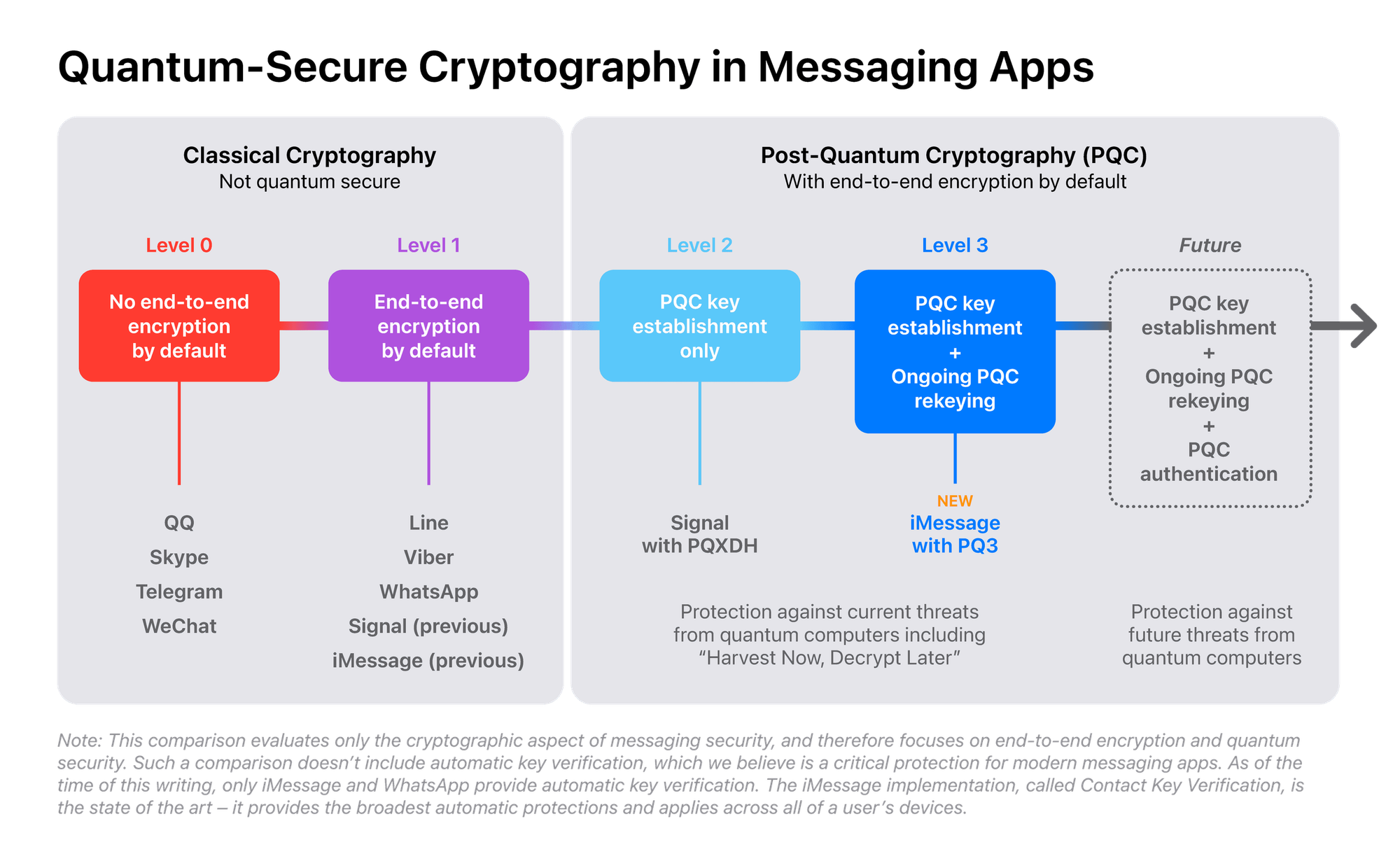
- Level 0: No end-to-end encryption by default (QQ, Skype, Telegram, WeChat)
- Level 1: End-to-end encryption enabled by default, but no post-quantum encryption (WhatsApp, Viber, Line, Signal (previous), iMessage(previous))
- Level 2: Post-quantum cryptography limited to initial key establishment
- Level 3: Post-quantum cryptography used for initial key establishment and ongoing message exchange with rapid re-keying (iMessage with PQ3)
Apple states that their new iMessage with PQ3 has "PQC key establishment plus ongoing PQC re-keying," meaning they're not just using one post-quantum key to encrypt the entire conversation. Instead, they're rotating the keys in a post-quantum way, re-establishing a new key approximately every 50 messages.
Apple's Explanation
Apple provides the following explanation for their level system:
"At level 2, the application of post-quantum cryptography is limited to the initial key establishment, providing quantum security only if the conversation key material is never compromised.
But today's sophisticated adversaries already have incentives to compromise encryption keys because doing so gives them the ability to decrypt messages protected by those keys for as long as the keys don't change.
To best protect end-to-end encrypted messaging, the post-quantum keys need to change on an ongoing basis to place an upper bound on how much of a conversation can be exposed by a single point-in-time key compromise, both now and with future quantum computers.
Therefore, we believe messaging protocols should go even further and attain level 3 security, where post-quantum cryptography is used to secure both the initial key establishment and the ongoing message exchange, with the ability to rapidly and automatically restore the cryptographic security of a conversation, even if a key becomes compromised."
Apple's Marketing Spin
While Apple's push for better encryption in iMessage is commendable, their blog post reeks of marketing spin, seemingly aimed at stealing the "post-quantum secure" thunder from Signal – an open-source encrypted messaging app.
Curiously, Apple mentions Signal five times throughout the post, despite Signal likely having far fewer users than apps like Skype, QQ, Telegram, WeChat, and even iMessage itself. This obsession with Signal suggests Apple feels threatened by the pioneering role Signal played in implementing post-quantum encryption months before Apple's PQ3 rollout.
The Reality: How Much Better is PQ3?
Apple wants to portray PQ3 as significantly more secure than Signal's post-quantum encryption, but the actual security gains are relatively minor when examined closely.
The "re-keying" mechanism Apple touts is more commonly referred to as "forward secrecy," a feature Signal has provided via the Double Ratchet algorithm for over 10 years. In fact, Signal's encryption algorithm with forward secrecy was open-sourced and copied by other messaging applications.
Moreover, Signal's post-quantum encryption algorithm with re-keying (key renewal) was implemented months before Apple's PQ3. Both use post-quantum encryption in addition to ECDH and employ the same Crystal-Kyber algorithm.
The only real difference is that PQ3 uses a post-quantum secure algorithm as part of the ratcheting process for key renewal, whereas Signal uses a classical (non-quantum) algorithm for this step.
So while Apple's PQ3 is technically more secure than Signal's implementation in this specific regard, the practical difference is minimal, especially considering Signal's encryption is open-source and has been scrutinized by cryptography experts for over a decade.
The False Promise of Security
Despite Apple's claims of superior security, iMessage's proprietary nature undermines its usefulness against "very strong adversaries who can corrupt parties or possess quantum computers and therefore defeat classical cryptography."
Secure messaging apps are just one tool in a broader security toolkit, and their effectiveness depends heavily on one's specific threat model. If the adversary is a government or global tech giant with access to quantum computing power, they're unlikely to waste resources brute-forcing stored encrypted messages.
Instead, such adversaries would likely deploy advanced techniques like the Pegasus spyware used to target iPhone users in the past. By compromising the device itself, any encrypted messages can be easily accessed.
For global-scale attackers, targeting Apple's closed-source platforms, deploying supply chain attacks, or corrupting software updates become more plausible attack vectors than directly breaking encryption.
The Importance of Open Source
In this context, the most crucial consideration – both now and in the post-quantum future – is the availability of open-source algorithms and messaging software that can be independently verified by users.
No matter how robust Apple's proprietary encryption protocols claim to be, users have no real control over the cryptographic keys or the devices generating them. The "iron fortress" of PQ3 is built upon the "weak proprietary sand" of Apple's closed ecosystem, which can be undermined if Apple or a third-party adversary corrupts it.
Conclusion
While Apple's addition of post-quantum encryption to iMessage is a positive step, the company's marketing spin and proprietary approach undermine its real-world security benefits against sophisticated adversaries.
For users prioritizing privacy and security, open-source solutions like Signal remain a more trustworthy and transparent option, as they allow independent verification and aren't beholden to the whims of a single company or corrupting influence.
Ultimately, robust encryption is just one piece of a comprehensive security strategy. True protection against quantum and classical threats alike requires a holistic approach incorporating open standards, verifiable code, and defense in depth – not merely trusting in the claims of a single vendor's "superior" proprietary solution.


