
We share more personal information online than ever before. From posting vacation photos on Instagram to checking in at a restaurant on Facebook, our online activities leave a trail of digital breadcrumbs about our lives.
While this level of sharing can enhance our connections and allow us to document precious memories, it also exposes us to privacy risks that few fully understand.
The rise of open source intelligence (OSINT) has made it alarmingly easy for anyone with modest technical skills to piece together these breadcrumbs and uncover startling amounts of personal information about us - from our locations and routines to the layouts of our homes.
Criminals and other bad actors can exploit this data for nefarious purposes like stalking, robbery, or worse. The tragic murder of rising rap star Pop Smoke in 2022 starkly illustrates the grave consequences of oversharing online.

By geotagging Instagram posts that revealed his rental home's address, the 20-year-old unwittingly enabled a robbery that turned deadly when he attempted to fight back. His senseless death serves as a sobering wake-up call about the importance of managing our digital footprints responsibly.
What is Open Source Intelligence (OSINT)?
Open source intelligence, or OSINT, refers to the practice of collecting and analyzing publicly available information to produce actionable data. In other words, it involves piecing together bits of openly accessible content and data from across the internet to reveal insights that may not be obvious when those fragments are viewed in isolation.
OSINT takes the stance that there is a wealth of information about people, organizations, and planned operations available in the public domain - scattered across website, public records, social media, and other open sources.
By aggregating and cross-referencing these dispersed pieces using specialized tools and techniques, OSINT practitioners can map out comprehensive profiles rich with privileged intelligence.
Professionals from fields like private investigation, law enforcement, and national security have long used OSINT as part of their work. However, the emergence of powerful OSINT tools that can crawl and correlate enormous datasets means these capabilities are now accessible to virtually anyone motivated to acquire them.
While OSINT has legitimate applications, bad actors can wield these techniques for criminal or malicious purposes like stalking, theft, fraud, and more. Armed with the ability to collate personal details at a granular level, bad actors can plan crimes with precision, putting individuals' privacy and safety at risk through absolutely no fault of their own.
Open Source Profiling: How Much Can Others Discover About You?
The amount of information available about you through OSINT may be shocking. Here's just a sample of what a motivated snooper could potentially learn:
- Your full name, date of birth, and other core personal/biographic details
- Home and work addresses, located with precision down to apartment unit numbers
- Family members' identities, occupations, etc.
- Details about your job/employer
- Photographs of you, your home, your vehicle(s), and more
- Your mobile numbers, email addresses, and online usernames/handles
- Passwords/credentials leaked through data breaches
- Your routine schedules and travel patterns
- Properties, assets, and financial records revealing your net worth
- Recreational interests, group memberships, and social connections
Much of this information is scattered across public data sources like social media sites, public records databases, business listings, online forums, and more. Individually, each piece seems innocuous. But aggregated, they comprise a high-resolution picture of your life - a virtual blueprint for physical and digital privacy violations.
For example, Jose Monkey is an OSINT educator on YouTube who crowdsources challenges from followers to locate them using only clues from photos and videos they share. In one viral case, Jose was able to pinpoint the exact home address of a mother who hoped the demonstration would caution her 10-year-old daughter about the risks of oversharing.
With just a few background glimpses of businesses and landmarks captured in her video, Jose cross-referenced store locator listings, mapped the spatial relationships using open source mapping tools, and identified the home's precise location down to the driveway - all from his computer. What may have seemed like forgettable background details enabled a shockingly accurate trace of her family's home.
Tactics like these, applied maliciously and combined with personal details seeded across innumerable data points online, could enable bad actors to perpetrate harassment, stalking, violent crimes, financial fraud, and more. As we'll explore, protecting your privacy hinges on stemming these data sources and limiting the trace you leave behind online.
Common Data Sources that Expose Your Personal Details
To get a handle on your digital footprint and harden your privacy, it's instructive to understand where and how your personal data surfaces across the public internet. Some common vectors include:
Metadata
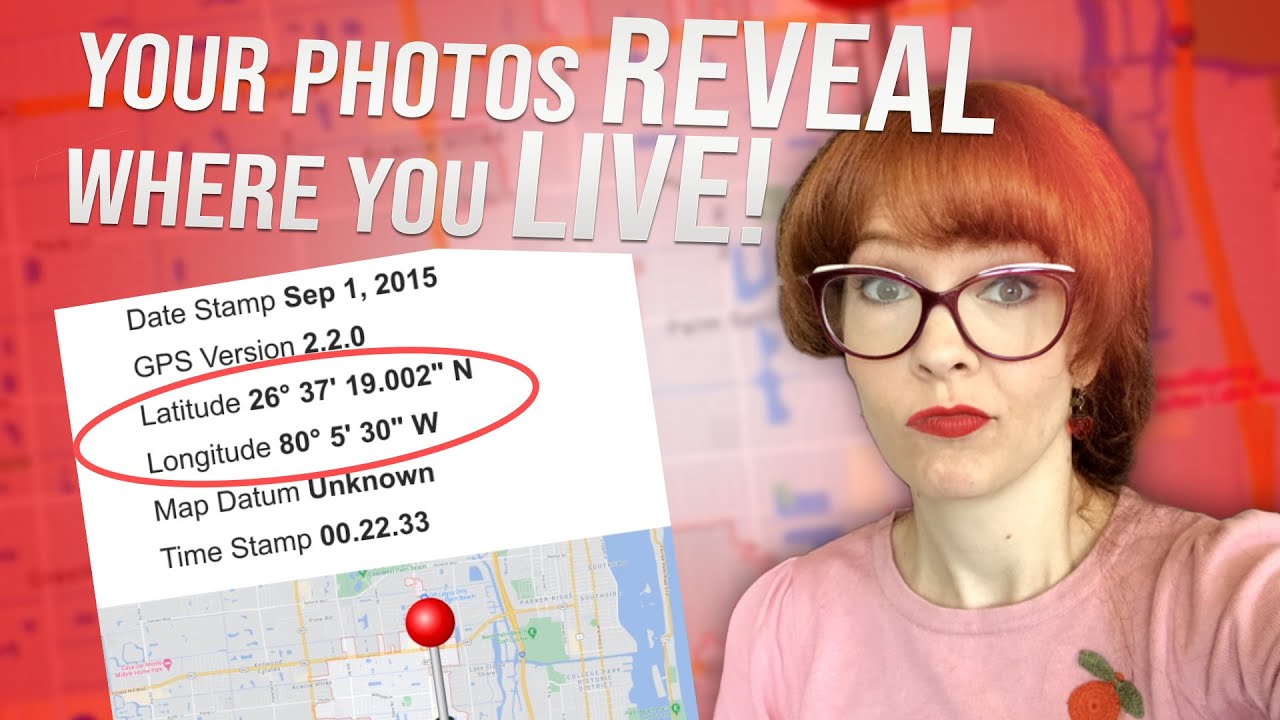
Even if we're cautious about the visible content of our posts, metadata – the hidden data embedded within digital files – can betray us without our knowledge. This metadata often includes GPS coordinates, timestamps, and other valuable information that can be exploited by those seeking to track our movements or activities.
While many social media platforms strip out location data before publishing content publicly, We cannot be certain about what happens to this information before it's removed:
Social Media Activity
These participatory platforms promote sharing personal moments, thoughts, locations, connections, and media like photos/videos. Geotags, tagged locations, activity check-ins, tagged photos of your home/car/etc., and other embedded metadata expose physical details about your life.
Shared opinions, commentary, usernames, quotes from posts, and other profile information betray details about your identity, job, interests, friend groups, and more.
Public Records & Data Brokers
These commercial services aggregate public records databases into searchable profiles. They vacuum up details from sources like court/legal filings, housing records, driving records, voter registration databases, and more into convenient digital dossiers that include names, birthdates, contact details, residential addresses, properties owned, liens/judgments, licenses, and more.
Records are frequently out-of-date or erroneous, but still routinely bought and sold between brokers for identity verification, background checks, marketing databases, and more nefarious purposes.
Online Footprints
Simply using the internet leaves digital breadcrumbs scattered across the web. These include accounts/profiles you sign up for using personal details, posts you leave across forums/comment sections, domain registration records tied to your name and personal information, mention of your name/likeness across news articles or other web publications, and more.
These scattered traces - frequently unintentional and long-forgotten - persist and can be rediscovered and reassembled.
Data Breaches & Leaks
When companies are hacked and user credential databases leak, your personal details like email addresses, usernames, passwords, payment information, and more can be exposed and added to databases circulated across the open internet and dark web. According to Have I Been Pwned, over 13 billion accounts have been implicated in known data breaches.

Cross-Referencing Data for Powerful Insights
OSINT tradecraft often focuses on cross-referencing information across disparate open sources to establish patterns, uncover linked details, and produce new revelatory insights. Its power lies in leveraging the pieces individually exposed across various platforms and databases to reassemble them into a unified, high-fidelity profile.
For example, an OSINT practitioner may start with a target's email address and use it to map out their online accounts and exposed personal data by looking for reuse of that email across site breaches, forum posts, leaked customer databases, and more.
With a full name gleaned from one of those sources, they could then surface employment details from professional networking sites or review sites, location data from public records and social posts, familial relationships based on shared addresses, contact details like phone numbers, and much more.
Each new piece of information potentially unlocks additional investigative pathways, allowing them to ripple outwards into a comprehensive personal profile. The depth and sensitivity of the compiled personal data quickly escalates.
By correlating information fragments scattered across dozens or even hundreds of sources, OSINT practitioners can pierce what may have initially seemed like robust privacy barriers.
OSINT Tools for Tracing Individuals Online
There is a robust ecosystem of powerful automated tools tailored to accelerate and systematize processes like the ones described above. While some require paid subscriptions, others are freely available online. Many leverage advanced technologies like facial recognition, phone number analysis, email lookups, and more to derive insights. Some notable examples include:
Username/Email Lookup Tools
These resources allow investigating targets' usernames, emails, and other identifiers across data breach dumps, online profiles, public web mentions, leak forums, and more to map out their digital footprint.
Examples: Have I Been Pwned, Dehashed
Public Records Aggregators
Subscription-based services aggregate public records databases and other commercial datasets to compile extensive profiles on targets containing names, addresses, phone numbers, relatives, property, ownership records, asset details, and more for background checks/monitoring services.
Examples: Truthfinder, Instant Checkmate, BeenVerified
Social Network Mapping Tools that scour social media accounts/profiles and then map out connections, activity patterns, interests, geotagged locations, etc. Help discern interests, affiliations, physical locations.
Examples: Osirix, Maltego
Code Search/Breach Monitoring Search engines for crawling code repositories, site data leaks, paste sites, etc. in order to uncover exposed intellectual property, credentials, personal data. Also enable constant monitoring.
Examples: Gitguardian, Gitleaks, Vigilante.pw
Internet/Darkweb Scanning Surface web crawlers and specialty search engines tailored for scouring deep/dark web sites, forums, repositories, data dumps, and other unindexed sources often missed by standard search engines.
Examples: IntelTechniques, Feng
Geospatial Mapping/Imagery Analysis Leverage mapping databases, satellite/aerial imagery, webcams/surveillance feeds to map out locations, model terrain, discern building/property details, monitor physical world settings. Examples: Google Earth Pro, Caltopo, Echosec
There are many more categories, including tools for scanning the internet of things, device/sensor analysis, maritime/aviation monitoring, crypto transaction de-anonymization, and more.
More resources for doing OSINT
We have barely scratched the surface and I would encourage you to explore more by doing searches on the internet because there re quite a number of resources and new ones come up everyday. One way to stay updated is subscribing to newsletters offered by some of the professionals as will as following them on X(Twitter)
With that said, here are some more resources put together by OSINT professionals:

The sophistication and scope of capabilities is vast, compounding the privacy implications of all our scattered data exhaust winding up correlated and reassembled this way.
Even if much of the underlying personal data originated from inadvertent oversharing, OSINT tools can transform those innocuous details into alarming dossiers that undermine our ability to remain private and anonymous online.
Protecting Your Digital Footprint
Given the reach of open source intelligence and how easily tiny crumbs of online data can cumulatively expose our personal lives, it's critical we get proactive about minimizing our digital footprints and managing what we broadcast across the internet. Here are some key steps everyone should take:
Conduct Regular Privacy Audits
Periodically review all your online accounts, profiles, posts, etc. and purge any overshared personal details, archives, or digital exhaust that could reveal sensitive data about you. Tighten privacy settings and leverage anonymity modes whenever possible when using apps/services.
This is often a tiresome and exhausting exercise and sometimes you may not get to all the information out there. Luckily, there are services out there that are designed to help in such a process such as DeleteME.

Mind Your Metadata
Photos, documents, videos, etc. frequently contain embedded metadata that can give away timelines, locations, device details, and other personal information about you. Scrub this metadata from files before posting them publicly. Here is a guide to get you started:
Use Encryption & Secure Tools
Leverage encryption for communications and cloud storage whenever possible. Use privacy-focused tools like encrypted messaging apps, VPNs, secure email services, and internet browsers optimized for minimizing trackable histories/footprints.
Be Discreet About Personal Data Sharing
Limit sharing of personally identifying information, credentials, birthdates, financial details, and other sensitive data across the internet as much as possible. Don't overshare routine locations, home addresses, travel plans, interests and affiliations in public forums.
Safeguard Physical World Privacy
Be mindful of settings that could expose your physical world whereabouts and activities. Disable geotagging on social apps, use secure personal WiFi networks, be cognizant of devices/sensors like webcams/digital assistants that could be surveilled, etc.
Practice Good Data Hygiene
Use strong unique passwords across accounts, leverage multi-factor authentication, and monitor for credential leaks/breaches. Minimize reuse of emails, usernames or shared personal details that could link various identity traces about you across data sources.
Limit Sharing of Visual Information
Be cautious about the visual details you share in photos/videos you post online - scenery, logos, text in backgrounds, etc. can reveal deeply personal details about your identity, relationships, workplace, home layouts and more.
While no single measure provides a magic privacy solution, maintaining vigilance across all these areas and adopting a privacy-first mindset for your online activities can mitigate much of your digital exhaust and blind spots that OSINT abuses prey upon. Recognizing our digital footprints are troves of insights about our personal lives is the first step towards reclaiming control of our privacy in this brave new open source world.
In subsequent blogs, we are going to cover some of these tools and techniques in detail. so be sure to stay subscribed so that you don't miss any of the posts.

