
The Tor Browser is one of the most widely used methods for accessing the dark web – a hidden part of the internet that is not indexed by search engines and can only be accessed using special software like Tor. The dark web hosts a wide range of content, from legitimate but privacy-focused websites to illicit marketplaces selling illegal goods and services.
While the dark web has gained notoriety for facilitating criminal activities, it also serves important purposes for those seeking anonymity and privacy online. Journalists, whistleblowers, activists, and individuals living under oppressive regimes rely on tools like Tor to communicate securely and access information freely.
The Tor Browser, being a gateway to the dark web, presents an intriguing subject for forensic analysis. Can using the Tor Browser leave behind digital breadcrumbs that could potentially reveal a user's activities on the dark web?
What is the Tor Browser?
The Tor Browser is a modified version of the Firefox web browser, designed to route internet traffic through the Tor network – a global network of volunteer relays that obscures the user's IP address and location, providing anonymity online.
When you access a website through the Tor Browser, your traffic is encrypted and bounced through multiple relay nodes before reaching its destination. This process makes it extremely difficult to trace the traffic back to its original source, protecting the user's identity and location.
To access websites on the dark web, also known as "onion sites" or "hidden services," you need to know the specific URL or address, which typically ends with the .onion top-level domain. These sites are hosted within the Tor network and are not accessible through regular web browsers.
The Tor Browser is available for various operating systems, including Windows, macOS, and Linux. It can also be run from live operating systems like Tails or Whonix, which are designed specifically for enhanced privacy and anonymity.
Whonix is a security-focused Linux distribution designed specifically for anonymous browsing and secure communications. It includes two virtual machines: the Whonix Gateway, which handles all network traffic through Tor, and the Whonix Workstation, where users can browse the web and run applications.
Forensic Artifacts and the Tor Browser
Cybersecurity researchers are particularly interested in understanding the forensic artifacts left behind by the Tor Browser. Forensic artifacts are digital traces or clues that can provide insight into a user's activities, potentially revealing the websites they've visited, the files they've downloaded, or even the information they've entered into web forms.
In the context of the Tor Browser, forensic artifacts could potentially reveal a user's activities on the dark web, including the onion sites they've accessed and any sensitive information they may have shared or downloaded.
Exploring Browser Artifacts: The Case of Mozilla Firefox
Web browsers like Mozilla Firefox are known to cache a significant amount of user data and browsing information. For instance, Firefox stores various artifacts in the user's AppData directory, including SQLite databases and internal cache files.
One of the most notable artifacts is the places.sqlite file, which contains a comprehensive history of visited websites, bookmarks, and form field data. This file is a prime target for information-stealing malware, as it can reveal sensitive browsing habits and potentially expose credentials or other sensitive information.
To illustrate this, we can utilize the SQLite Database Browser tool to open and examine the contents of the places.sqlite file. Upon doing so, we can access a detailed record of our browsing history, including visited URLs, timestamps, and other metadata.
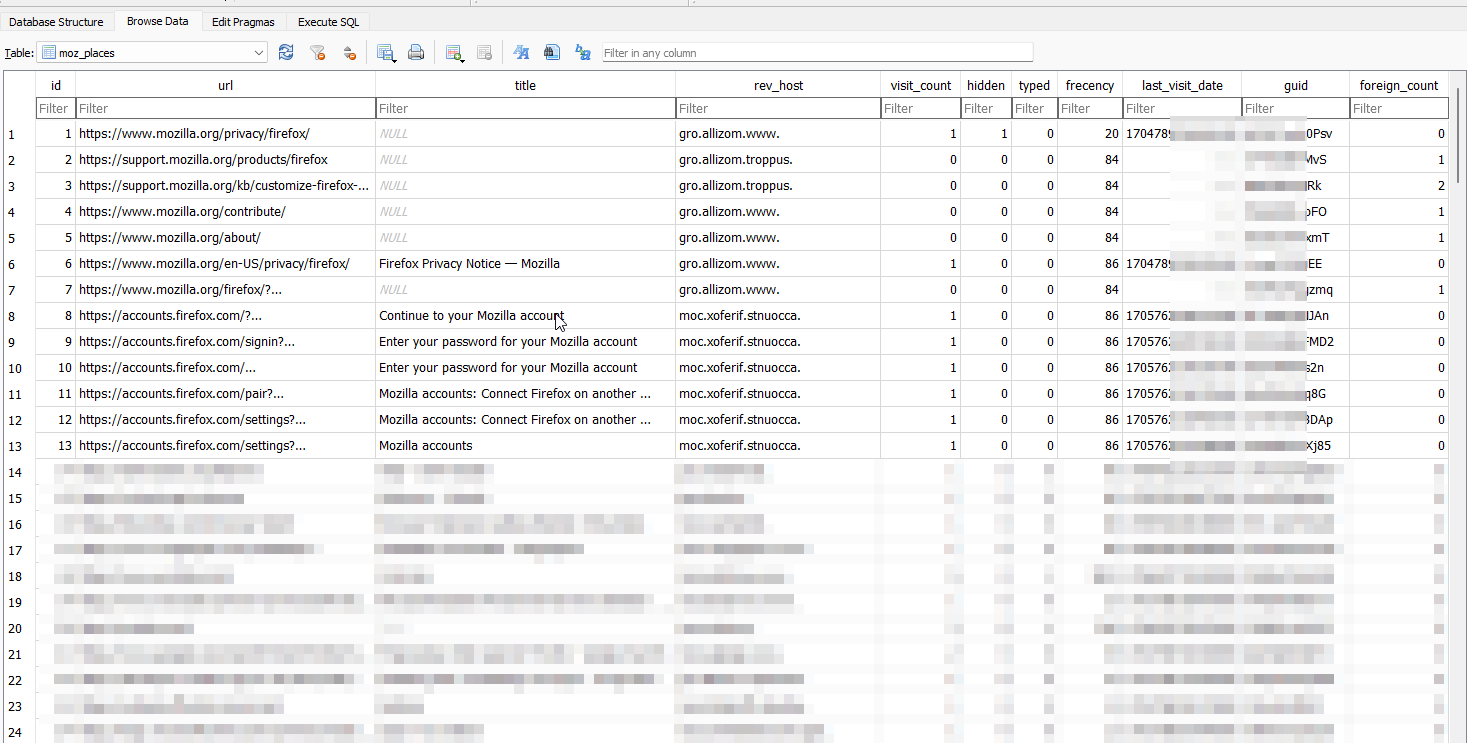
Examining the Tor Browser's Artifacts
Since the Tor Browser is built upon an extended release of Firefox, it shares some similarities in its internal structure and file organization.
Within the Tor Browser's installation directory, we can find a familiar structure, including a data folder, a browser subdirectory, and even the presence of the places.sqlite file within the profile folder.
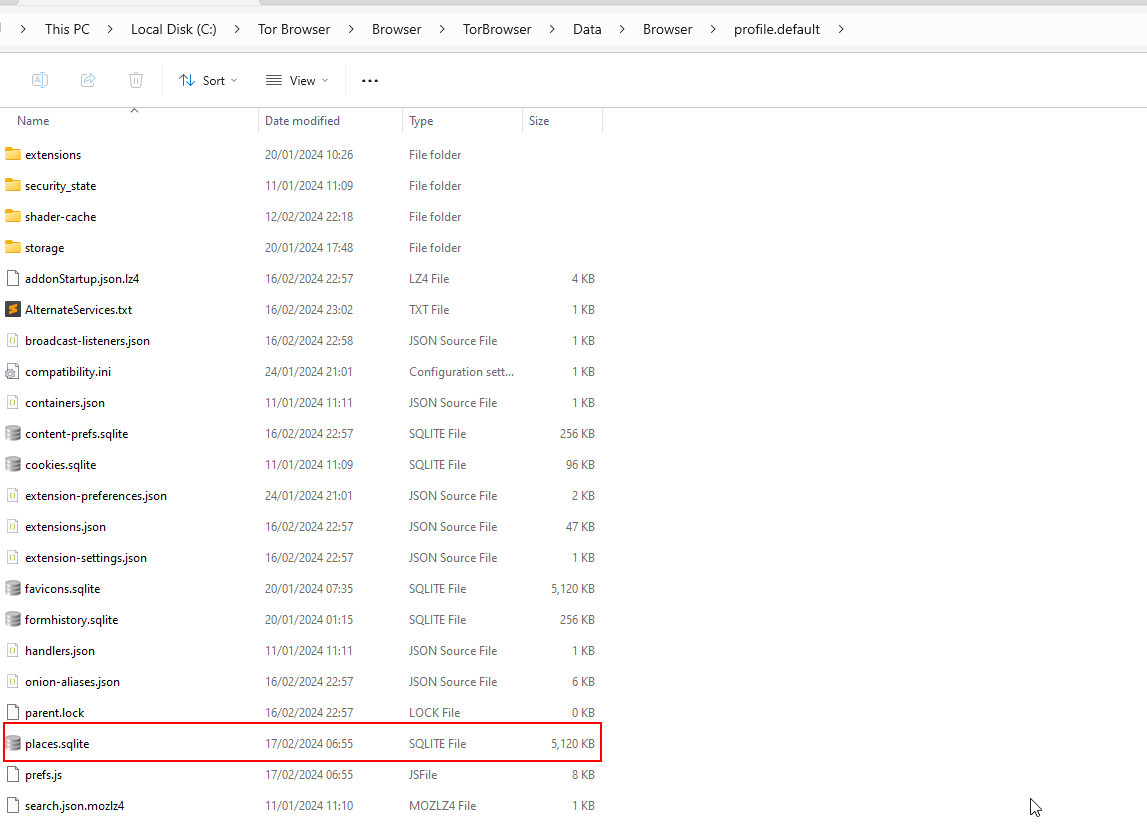
However, upon closer inspection, the contents of the places.sqlite file reveal a stark contrast from its counterpart in Mozilla Firefox. While the file exists, it appears to contain only default onion links and no recorded history of the actual websites or onion addresses visited during our Dark Web exploration.

To validate this observation, you can check the contents of the tor browser folder on both Linux and Windows environments, opening the Tor Browser and visiting various onion sites. Despite this activity, the places.sqlite file remained devoid of any recorded history or metadata beyond the default entries.
This finding suggests that the Tor Browser, by design, does not store or cache the user's browsing history within its internal files, at least not in the conventional manner observed in traditional web browsers like Firefox.
Additional Forensic Artifacts: State Files and Registry Entries
While the absence of browsing history in the places.sqlite file is a noteworthy discovery, Researchers and security professionals have identified other potential sources of information related to Tor Browser usage.
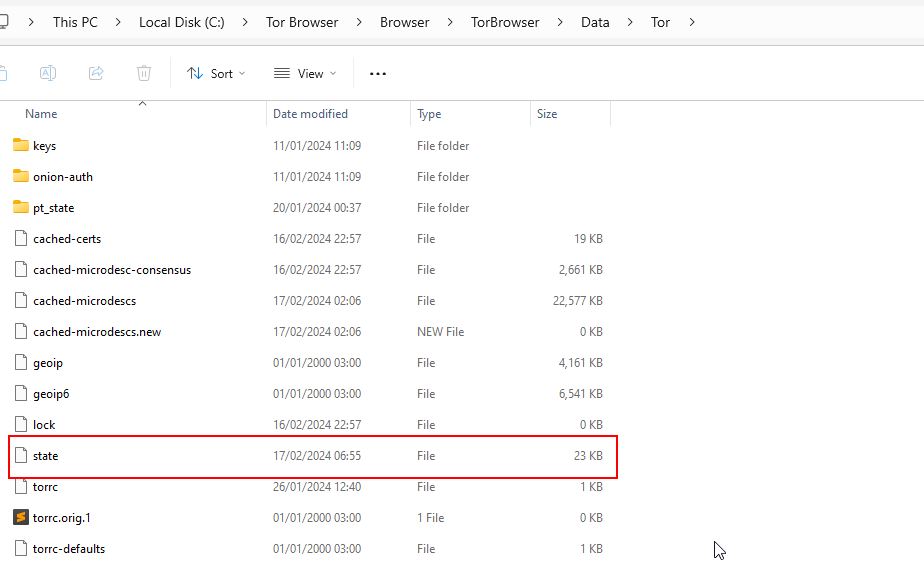
One such artifact is the state file, located within the tor subdirectory of the Tor Browser's installation folder. This file contains timestamps indicating the last time the Tor network was utilized, providing a rough estimate of when the Tor Browser was last active.
On Windows systems, the Windows Registry can also yield clues about the installation and usage of the Tor Browser. By exploring the registry with an advanced tool like RegCool, we can locate keys and entries related to the Tor Browser, including shell bag entries and information about the Tor Project Firefox launcher.
Other potential artifacts discussed in various research papers include prefetch files, memory dumps (which could be analyzed using tools like Volatility), and network traffic captures (although the contents of Tor traffic would be encrypted and obfuscated).
The Importance of Anonymity and Privacy
While the discovery of potential forensic artifacts is intriguing from a technical and investigative standpoint, it is crucial to acknowledge the importance of anonymity and privacy tools like the Tor Browser. These tools play a vital role in enabling free speech, protecting whistleblowers, and safeguarding the online identities of individuals and organizations facing censorship or oppression.
The absence of detailed browsing history within the Tor Browser's internal files can be seen as a positive feature, designed to uphold the principles of anonymity and privacy that the Tor network was built upon. It is a trade-off between forensic transparency and the protection of user privacy, a balance that must be carefully considered and respected.
Responsible Use and Ethical Considerations
Throughout our exploration, it is essential to emphasize the responsible and ethical use of tools like the Tor Browser and the avoidance of any illicit or malicious activities. While the Dark Web harbors a wealth of information and opportunities for research, it is also a realm that can attract nefarious actors and facilitate illegal activities.
We strongly discourage the engagement in any form of cybercrime, hacking, or the distribution of malware, ransomware, or other malicious code. Our investigation into the Tor Browser's forensic artifacts is conducted solely for educational and research purposes, with the aim of understanding the technical aspects and privacy implications of this widely used tool.
Conclusion
While traditional web browsers like Mozilla Firefox leave behind detailed browsing histories and artifacts, the Tor Browser appears to prioritize user privacy by refraining from storing such information within its internal files.
However, our investigation revealed other potential sources of forensic information, including state files, Windows Registry entries, and network traffic analysis. These artifacts, while limited in their ability to reveal specific onion addresses or visited sites, can still provide insights into the installation, usage, and activity timestamps of the Tor Browser.

To make it even harder for such information to be useful, you can connect to a reliable VPN first and then connect to the Tor network. And yes, it is recommended to connect to a VPN first and then connect to the Tor network, make sure to use a reliable VPN provider in the process.

Fell free to drop your comments below or drop us an email at: [email protected]



