
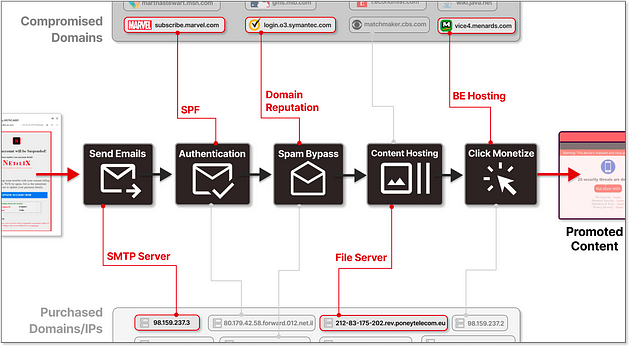
Cybersecurity researchers at Guardio Labs, have unveiled a new attack dubbed SubdoMailing, which is a massive spam operation that leverages hijacked subdomains of major brands and institutions to bombard users with millions of malicious emails daily.
The campaign has been ongoing since at least 2022 and has compromised over 8,000 domains and 13,000 subdomains belonging to esteemed companies, educational institutions, and media organizations, including Microsoft, VMware, McAfee, The Economist, Cornell University, CBS, Marvel, and eBay, among others.
The campaign's success lies in its ability to exploit the trust and credibility associated with these well-known brands, using their hijacked subdomains to bypass email security measures and deliver spam and phishing emails directly to users' inboxes.
Also Read:

The Anatomy of the SubdoMailing Campaign
The SubdoMailing campaign is a large-scale operation that relies on two primary methods for hijacking subdomains: exploiting dangling CNAME records and abusing forgotten SPF (Sender Policy Framework) records. Let's explore each of these techniques in detail.
Exploiting Dangling CNAME Records
A CNAME (Canonical Name) record is a type of DNS (Domain Name System) record used to redirect one domain name to another. For example, a company might use a CNAME record to direct a subdomain like "promo.company.com" to an external domain hosting a promotional website, such as "company2020promo.com".
However, when a promotional campaign or project ends, companies often fail to remove the corresponding CNAME records, leaving them "dangling" and vulable to exploitation. The threat actors behind the SubdoMailing campaign actively scan for these abandoned domains and quickly re-register them, gaining control over the associated subdomains in the process.
If a subomain has a CNAME record, the subdomain inherits the entire behavior of the domain it is pointing to , including it’s SPF policy.
Once they have control over a hijacked subdomain like "promo.company.com", the cybercriminals can authorize their own mail servers to send emails from that subdomain, effectively inheriting the reputation and trust associated with the parent domain, "company.com". This technique allows them to bypass email security measures and increases the likelihood that their spam or phishing emails will be delivered to users' inboxes.
Abusing Forgotten SPF Records
The second method employed by the SubdoMailing campaign involves exploiting forgotten SPF (Sender Policy Framework) records. SPF is an email authentication system that helps prevent email spoofing by verifying that the email is being sent from an authorized IP address or domain.
Large organizations often include multiple IP addresses and external domains in their SPF records to accommodate various email services, mass mailing tools, user survey platforms, and other third-party providers. However, as companies evolve and change their service providers over time, they may forget to remove outdated or expired domains from their SPF records.
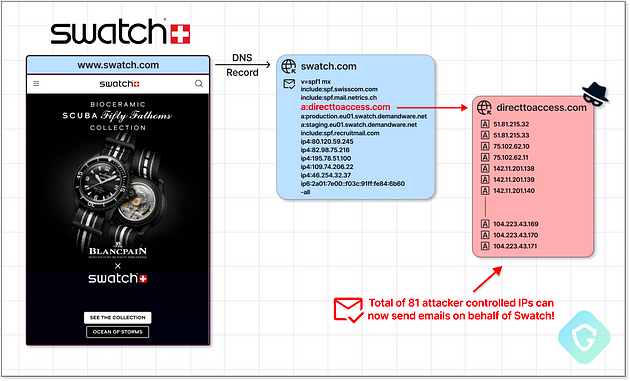
The threat actors behind SubdoMailing actively search for these forgotten domains and quickly re-register them. By doing so, they gain the ability to send emails not just from a subdomain but from the primary domain itself, leveraging the full trust and reputation of the hijacked organization.
For example, if a company's SPF record includes an abandoned domain like "customersurveytool.com", which was previously used for user surveys, the attackers can register that domain and gain the ability to send emails from the company's primary domain, such as "company.com". The attacker would have multiple IP addresses linked to the domain that has been registered and therefore the IP addresses would be recognised as legitimate.
How bad is the situation?
When Guardio published the research, they had identified over 8,000 domains and 13,000 subdomains that have fallen victim to this exploitation, with the numbers growing by the hundreds each day. Even more alarming is the estimated volume of malicious emails being sent daily, which researchers peg at around five million.
To avoid detection and maintain the effectiveness of their operation, the threat actors behind SubdoMailing employ a sophisticated rotation system. Each hijacked domain is typically used for spam distribution for only 1-2 days before going dormant for an extended period. During this active window, the domain is used to send vast quantities of spam and phishing emails, leveraging the credibility of the associated brand or institution.
After a couple of days of intense activity, the domain is temporarily retired, and the attackers switch to the next hijacked domain in their arsenal. This constant rotation helps the cybercriminals evade spam filters and maintain a steady stream of malicious emails reaching unsuspecting users.
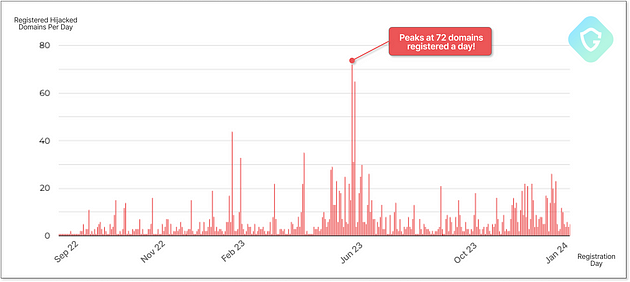
The record for the highest number of hijacked domains exploited in a single day stands at a staggering 72, which occurred in June 2023, highlighting the scale and sophistication of this operation.
Techniques and Tactics
Researchers at Guardio Labs dissected a particularly insidious email that alerted recipients of suspicious activity within a cloud storage account. This email, cleverly crafted as an image to bypass text-based spam filters, created a sense of urgency and prompted the recipient to take action.
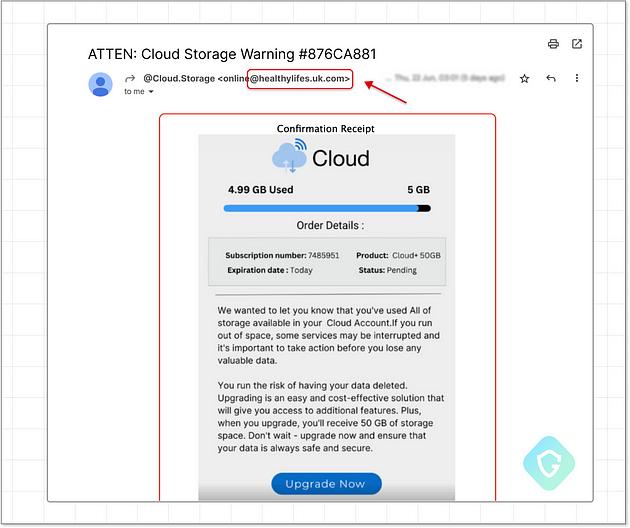
A closer examination of the email headers revealed some intriguing insights:
- The email's headers showed that it passed industry-standard authentication protocols, including the Sender Policy Framework (SPF), DomainKeysde Intified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC). These protocols are designed to prevent email spoofing and ensure the authenticity of the sender.
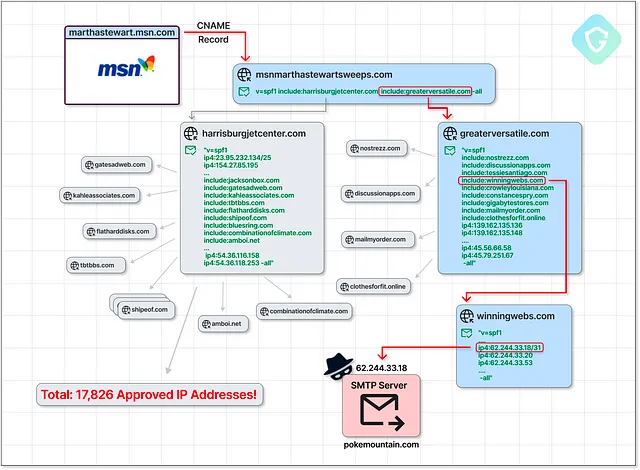
- The email originated from an SMTP (Simple Mail Transfer Protocol) server located in Kyiv, Ukraine, yet it was flagged as being sent from the legitimate email address "return_ulkvw[@]marthastewart.msn.com".
Upon interacting with any part of the email, the recipient is through a series of click-redirects across different domains, each designed to check the user's device type and geographic location. Depending on these factors, the recipient could be directed to various malicious content, including annoying advertisements, affiliate links, quiz scams, phishing sites, or even malware downloads aimed at stealing sensitive information or extorting money.
This seemingly legitimate email address which appeared to be associated with Martha Stewart and Microsoft's MSN portal was due to the subdomain "marthastewart.msn.com" which had been hijacked through a clever exploitation of a long-forgotten promotional campaign.
With control over this hijacked subdomain, the cybercriminals engineered an intricate SPF record that included a staggering 17,826 IP addresses, all authorized to send emails on behalf of "marthastewart.msn.com".
This complex SPF record was designed to bypass email security measures and lend credibility to the malicious emails sent from the hijacked subdomain, leveraging the trust and reputation associated with Microsoft's MSN portal.
So what are the dangers?
Financial Losses and Data Breaches
One of the primary goals of the SubdoMailing campaign is to distribute spam and phishing emails on a massive scale. These emails often contain malicious links or attachments designed to trick recipients into revealing sensitive information, such as login credentials, financial details, or personal data.
If successful, these phishing attacks can lead to financial losses, identity theft, and data breaches, compromising the privacy and security of individuals and organizations alike. Businesses may suffer from reputational damage, regulatory fines, and costly remediation efforts in the aftermath of a successful attack.
Malware Distribution and System Compromise
In addition to phishing, the SubdoMailing campaign has been observed distributing various forms of malware, including trojans, ransomware, and other malicious payloads. These malicious programs can infiltrate systems, steal data, encrypt files for ransom, or even establish persistent control over compromised devices.
For businesses and organizations, a successful malware infection can lead to significant operational disruptions, data loss, and potentially crippling financial consequences, particularly in the case of ransomware attacks. The costs associated with system recovery, data restoration, and potential legal liabilities is extremely high.
Reputational Damage and Loss of Trust
Perhaps one of the most insidious consequences of the SubdoMailing campaign is the erosion of trust in legitimate brands and institutions. When users receive malicious emails purportedly from trusted sources like Microsoft, VMware, or Cornell University, it can severely undermine their confidence in these organizations.
This loss of trust can, affecting customer relationships, stakeholder confidence, and the overall reputation of the affected brands. Rebuilding this trust can be a lengthy and challenging process, potentially leading to significant financial losses and long-term damage to an organization's credibility.
Protecting Yourself and Your Organization
Given the scale and sophistication of the SubdoMailing campaign, it is crucial for individuals, businesses, and organizations to take proactive steps to safeguard their online presence and mitigate the risks associated with subdomain hijacking. Here are some key recommendations:
1. Properly Implementing Email Authentication Protocols
Implementing email authentication protocols, such as SPF, DKIM, and DMARC, is essential for protecting your organization's email infrastructure and preventing spoofing attacks. These protocols help verify the authenticity of email senders and provide a framework for identifying and blocking unauthorized emails.

You should also regularly check and remove records that are no longer in use, especially if you authorize third parties to send emails on your behalf.
2. Regularly Audit and Maintain Your Domain Assets
Conduct regular audits of your organization's web resources, including domains, subdomains, and associated DNS records. Identify and remove any outdated or unused assets, such as expired domains or dangling CNAME records, to prevent their exploitation by cybercriminals.
3. Stay Vigilant and Educate Employees
Educate your employees on the dangers of phishing attacks and the importance of verifying the legitimacy of emails, particularly those requesting sensitive information or prompting urgent action. Encourage a culture of skepticism and promote the reporting of suspicious emails to your organization's security team.
4. Use Robust Email Security Solutions
Invest in robust email security solutions that can detect and block malicious emails, including those leveraging hijacked subdomains or spoofed addresses. These solutions often employ advanced techniques, such as machine learning and real-time threat intelligence, to identify and mitigate emerging threats effectively.
5. Monitor and Respond to Security Incidents
Establish a comprehensive security incident response plan that outlines the steps to be taken in the event of a potential breach or security incident. This should include procedures for investigating and containing the incident, notifying relevant parties, and implementing necessary remediation measures.
Is my business vulnerable to SubdoMailing?

Gurdio have created a special “SubdoMailing” checker website, allowing domain administrators and site owners to quickly check if any trace of abuse was found by our systems — and get the relevant info needed to fix and prevent this.




