
Passkeys are a type of login credential based on public-key cryptography, which eliminates the need for traditional passwords. Instead of memorizing and entering complex passwords, users can authenticate their identities using biometrics (such as fingerprint or facial recognition) or a device PIN.
At their core, passkeys consist of two interlinked components: a private key and a public key. The private key remains securely stored on the user's device and is never shared with the website or application being accessed. The public key, on the other hand, is shared with the service provider and serves as a unique identifier for the user's account.
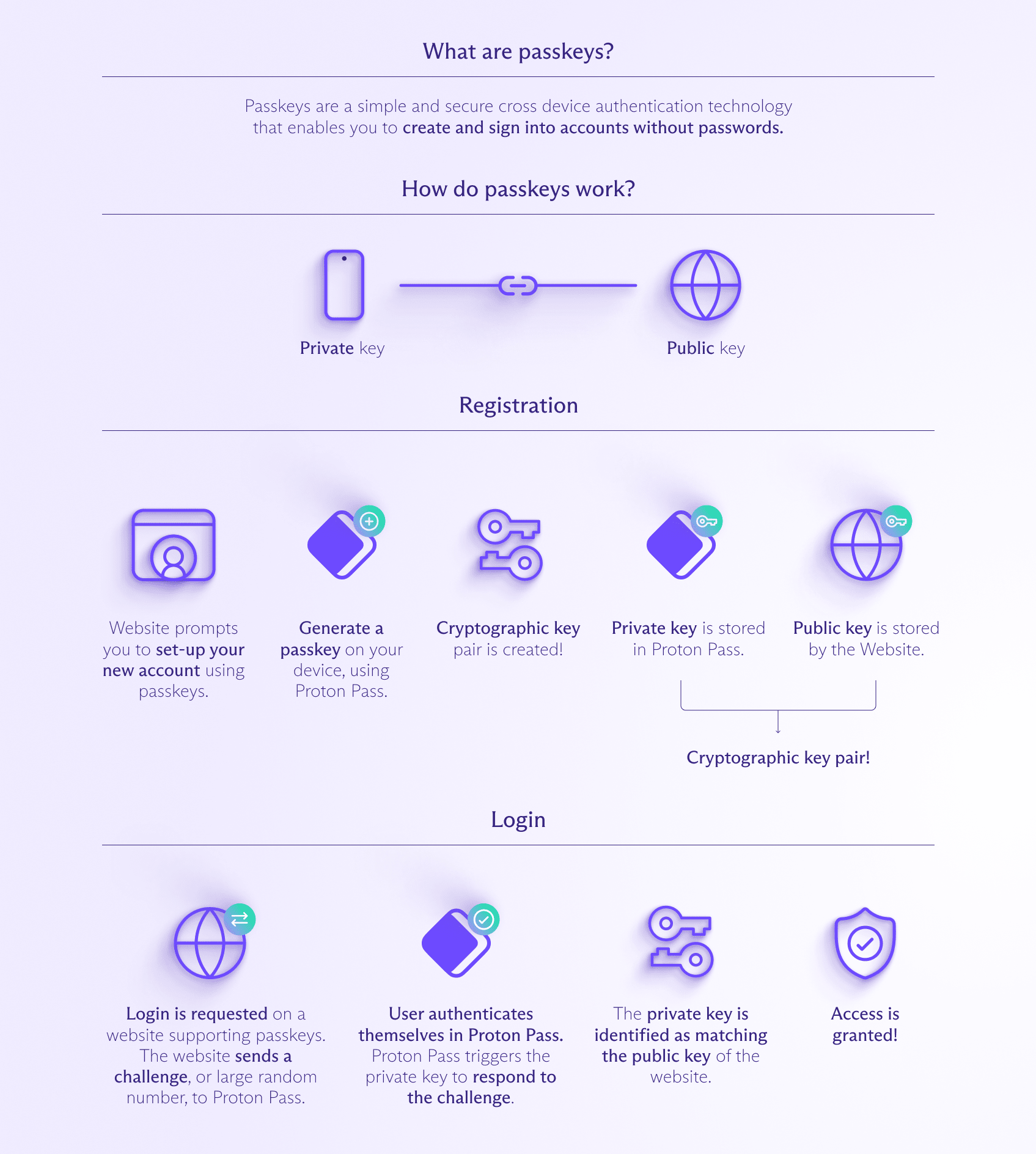
When a user attempts to log in to a service that supports passkeys, the website or application generates a cryptographic challenge. The user's device then signs this challenge using the private key, and the resulting signature is sent back to the service provider. The service provider verifies the signature using the user's public key, authenticating the user's identity without ever needing to transmit or store the private key.
This process is facilitated by the WebAuthn (Web Authentication) standard, developed by the FIDO Alliance (Fast IDentity Online), a consortium of leading technology companies dedicated to creating secure and user-friendly authentication solutions.
How Passkeys Work
Public-Key Cryptography
Passkeys leverage the principles of public-key cryptography, a widely used and robust cryptographic system. In this system, each user has a pair of mathematically related keys: a private key and a public key.
The private key is a secret, unique value that is securely stored on the user's device and never shared with anyone else. This private key is used to sign or decrypt data, proving the user's identity.
The public key, on the other hand, is derived from the private key using complex mathematical algorithms. The public key can be shared freely and is used by service providers to verify the user's identity by validating the signature or encrypted data generated using the corresponding private key.
The Passkey Authentication Process
When a user attempts to log in to a website or application that supports passkeys, the following process occurs:
- The website provides your browser with a challenge to complete.
- Your browser asks your device holding the private key to sign the challenge data.
- This signature derived from the private key gets sent back to the website.
- The website verifies the signature matches the public key it has on file for your account.
If the signature is valid, you're authenticated - without any password being transmitted or stored by the website! The website never gains access to your private key, which is the critical factor, authenticating you.
The real magic is that this private key is locked to a specific device and release factor like biometrics or a PIN. Even if an attacker manages to obtain the public key and signed challenge response, without the private key anchored to your device and biometrics, the credential cannot be used.
Advantages of using passkeys Passkey
Proponents highlight several major benefits that passkeys provide over traditional password authentication:
No Shared Secrets
With passwords, the same secret is stored by the client and server, introducing risk if either is compromised. With passkeys, the private key for authentication never leaves the user's trusted devices.
Phishing Resistance
Since passkeys are isolated to individual websites and devices, they cannot be phished or replayed across sites. A phished passkey simply won't work anywhere else.
No More Passwords to Remember
Passkeys utilize device capabilities like biometrics or PINs rather than usernames and passwords that must be created, remembered, and typed.
Inherent Multi-Factor
Every passkey interaction utilizes something you have (the private key locked to your device) and something you are (your biometrics) or know (PIN). Multifactor is built-in by default.
Portability Across Devices
You can use passkeys on numerous devices like phones, tablets, laptops - your credentials will sync and roam securely between them in the cloud, especially with the use of password managers that support passkeys.
The passkey security model is compelling - so much so that major industry titans like Apple, Google, Microsoft, and Amazon have all rallied around passkeys as the future replacement for passwords.
Creating and Using Passkeys
Most major platforms like Windows, macOS, Android, and iOS now offer native support for creating, storing, and autofilling passkeys right from the operating system. But apps like password managers also provide this functionality with additional convenience and management capabilities.
Passkey Synchronization and Recovery
One of the key advantages of using passkeys with password managers like 1Password and Bitwarden is the ability to securely synchronize and recover passkeys across multiple devices.
When a user creates a new passkey, the password manager stores and encrypts the private key, allowing it to be safely synced and accessed from other devices associated with the user's account. This ensures a seamless experience, as users can log in to their accounts using passkeys from any of their devices without the need to re-create the passkey.
In case a user loses access to their primary device or encounters other issues, password managers also provide mechanisms for passkey recovery. This process typically involves verifying the user's identity through additional authentication factors, such as biometrics or secondary devices, before granting access to the encrypted private keys.
Passkeys vs. Traditional Passwords
While passkeys offer numerous advantages, it's important to understand how they compare to traditional password-based authentication methods. Here's a side-by-side comparison:
| Passkeys | Traditional Passwords | |
|---|---|---|
| Security | Highly secure, resistant to phishing and difficult to steal | Vulnerable to various attacks like phishing and data breaches |
| User Experience | Seamless, no need to remember or type in credentials | Cumbersome, users must create and remember complex passwords |
| Cross-Platform | Designed for cross-platform support and interoperability | Platform-specific challenges in maintaining consistent UX |
| Account Recovery | Secure recovery mechanisms using additional factors | Potential security risks with password reset mechanisms |
| Implementation | Requires support from service providers and device vendors | Widely implemented, but becoming increasingly outdated |
While passwords have served as the industry standard for authentication for decades, their inherent weaknesses have become increasingly apparent in the modern digital landscape. Passkeys address many of these shortcomings, offering a more secure and user-friendly alternative for authenticating identities.
Challenges and Adoption Considerations
Despite the numerous benefits of passkeys, their widespread adoption is not without challenges. Here are some considerations that need to be addressed:
Compatibility and Interoperability
While major technology companies have committed to supporting passkeys, ensuring seamless interoperability across various platforms, devices, and service providers remains a challenge. Consistent implementation and adherence to open standards like WebAuthn are crucial to avoiding fragmentation and providing a unified user experience.
User Education and Adoption
Introducing new authentication methods often requires significant user education and awareness efforts. While passkeys offer a more convenient login experience, users accustomed to traditional passwords may be hesitant to adopt a new technology. Clear communication and guidance from service providers and technology companies will be essential to facilitate widespread adoption.
Legacy System Integration
Many existing applications and systems were designed with password-based authentication in mind. Integrating passkey support into these legacy systems may require substantial development efforts and resources, potentially slowing down adoption rates.
Backup and Recovery Mechanisms
While password managers offer secure mechanisms for passkey backup and recovery, ensuring these processes are robust, user-friendly, and widely adopted will be crucial. Users must have confidence in their ability to regain access to their accounts and data in the event of lost or compromised devices.
Regulatory Compliance and Industry Standards
Certain industries and sectors, such as finance and healthcare, may have specific regulatory requirements or industry standards related to authentication methods. Ensuring that passkeys meet these requirements and are compliant with relevant regulations will be necessary for their adoption in these domains.
Getting Started with Passkeys
While passkeys are still in the early stages of adoption, several popular websites and applications already support this technology. Password managers like 1Password, Bitwarden and Protonpass have also integrated passkey support, making it easier for users to manage and use passkeys across multiple devices and accounts.
1Password
1Password, a renowned password manager, has been at the forefront of passkey adoption. With their latest releases, 1Password now supports creating, saving, and signing in with passkeys on desktop browsers, iOS devices running iOS 17 or iPadOS 17, and Android devices. Additionally, 1Password allows you to view, manage, and share your saved passkeys across all your devices, ensuring a seamless passkey experience.
To get started with passkeys in 1Password, simply visit a website that supports passkeys and follow the prompts to create a new passkey or use an existing one. 1Password will guide you through the process and securely store your passkey alongside your other sensitive information.
Bitwarden
Bitwarden, another popular open source password manager, has also embraced passkey technology. With their latest browser extension updates, Bitwarden now supports storing and logging in with passkeys on supported websites.
To use passkeys with Bitwarden, visit a compatible website and follow the prompts to create or sign in with a passkey. Bitwarden will securely store your passkey and handle the authentication process for you.
Protonpass
Proton Pass is more than a tool to securely save passwords and automate logging in. It's also an identity manager that generates unique email aliases, preventing your true email address from being used to track you, exposed in data breaches, or targeted for spam.
Proton Pass supports passkeys on all devices and plans!


