Linux is one of the most widely used operating systems, powering a vast array of servers, supercomputers, embedded systems, IoT devices and increasingly personal computers and mobile devices as well. While its open source nature provides many advantages in terms of customizability, auditing, and transparency, it also means Linux must be properly secured to prevent potential vulnerabilities from being exploited.
Linux is not inherently more or less secure than other operating systems like Windows. Linux tends to be less targeted on personal computers since it has a smaller market share compared to Windows. However, Linux is very popular on servers, so it represents an attractive target for hackers.
There has been an increase in Linux vulnerabilities, according to reports from organizations like Crowdstrike and The National Vulnerability Database (NVD). For instance, 1,958 Linux vulnerabilities were discovered in 2020. Malware targeting Linux systems increased by 35% in 2021 compared to 2020. Furthermore, there were about 1.7 million new Linux malware infections in 2022—a 650% rise from the year before. Ultimately, the level of security depends on how the system is configured and maintained.
Reduce your Attack Surface by Removing Unused Software
Install less software and remove unused software
One of the most impactful steps you can take is reducing your system's "attack surface" by removing any unused or unnecessary software packages and services. Every additional package and running service introduces potential vulnerabilities that attackers could exploit. It's recommended to carefully review all installed packages and remove anything you know you are not using.
Different Linux distributions use different package managers and have different ways of removing packages and software. For instance, in Debian/Ubuntu systems, you can automatically remove unused packages dependencies with sudo apt autoremove. Here is a guide to get you started with removing unwanted software.


Stop and disable unused services
You should also stop and disable any services you don't need running in the background, for example, printing (CUPS), audio playback (ALSA), Bluetooth, etc. Listing services and stopping/disabling them is relatively easy in most distributions that use systemd.
To list all running services, you can use systemctl list-units --type=service --state=running. Using systemctl stop and systemctl disable allows stopping services without removal, so they can be re-enabled if needed later. Removing excessive packages and non-essential services significantly shrinks the number of avenues attackers have to infiltrate your system.
For servers that do not require graphical desktop environments, it is best to avoid running X11 or other desktop packages, such as Wayland, which significantly increase the attack surface without providing value. SSH provides a secure remote access alternative.
Keep Software Updated and Patch Vulnerabilities
Keeping all software and packages on your system fully updated and patched is another core security practice. You need to ensure that your entire Linux system is always fully up to date to eliminate the bulk of exposure to common exploits. Many distributions also offer live patch services that can patch vulnerabilities while the server is still running for the most critical issues.
Outdated software is vulnerable software. Hackers actively search for and exploit known vulnerabilities in unpatched software. While software updates can sometimes be annoying on other platforms, on Linux they are designed not to disrupt workflows. Most desktop distributions even auto-update by default. However, it's important to still manually check for and apply any available updates on server systems which may not auto-update.
Use Strong Authentication Mechanisms
Use SSH keys instead of passwords.
Ideally, authentication for SSH and other services should use public-key encryption instead of passwords for added security. You can also add multifactor authentication (MFA) via an authenticator app for accounts that require stronger protection. Just be sure to properly secure any private keys, like storing them encrypted or using a security key.
Use strong and unique Passwords
Weak or reused passwords are still one of the biggest vulnerabilities organizations and individuals face. When securing a Linux system, focus on enforcing strong, unique passwords for all user accounts and services. Things like minimum password length, complexity rules, and account lockout policies after failed login attempts help strengthen credentials. Ongoing password auditing and rotation can further reduce risk from exposed or cracked credentials.
Alternatively, you can use third party remote access tools, that eliminate the need for exposing your server to the internet but instead provides a good way of authenticationa and eliminates dangers such as bruteforcing or those brough about by bots. A good example of such a tool is Teleport, which is an Open Infrastructure Access Platform.

Harden User Accounts and Access Control
Proper user account management forms another core layer of defense. Some key steps include disabling local login for the powerful "root" superuser account and instead using sudo privileges for administrative tasks. This enforces the principle of least privilege
OpenSSH server is usually the default SSH server program for most Linux distributions, and it can be accessed in order to remotely administrate Linux servers over SSH. Because your OpenSSH server serves as your server's front door or entry point, it is crucial that you secure it properly.
Full Disk Encryption for Endpoint Protection
Full disk encryption (FDE) using LUKS or similar technologies provides an invaluable layer of protection for laptops, workstations and servers, that may be physically accessed or stolen. With an encrypted disk, even if an unauthorized person gains physical access, without the passphrase they cannot access any user or system data on the drive. FDE prevents tampering, data theft, or insertion of malware even with physical device possession.
It's recommended to enable encryption during Linux installation and remember your password, as without it, you risk losing access to the encrypted drive contents. Some distributions also allow post-install disk encryption. Using a long, randomized passphrase protects against brute force attempts. Carefully backing up your decryption passphrase is also critical for disaster recovery.
Different Linux distributions have different ways of doing full disk encryption, and you can find the guides below.



Harden the Linux Kernel for Added Security
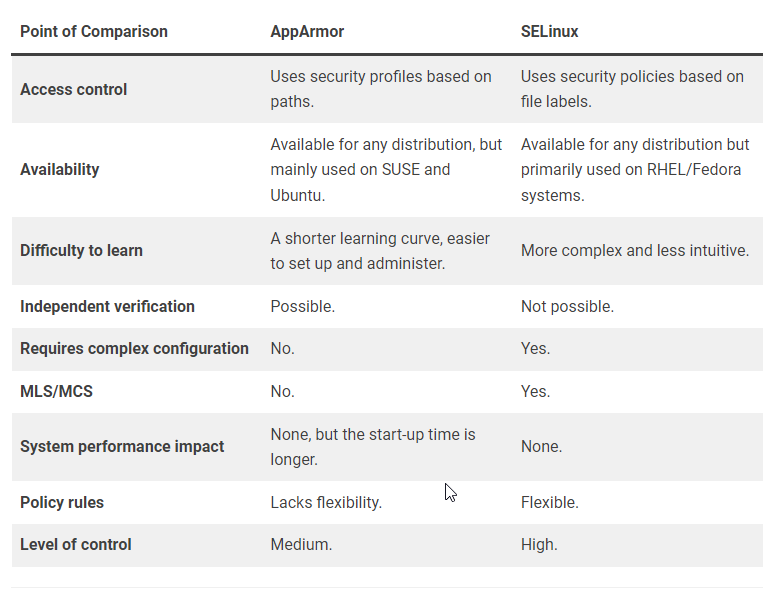
Most Linux distributions also include Mandatory Access Control (MAC) systems like AppArmor on Debian/Ubuntu or SELinux on RedHat-based systems. These work to enforce additional fine-grained access policies system-wide beyond standard Linux permissions.
Configuring security features directly in the Linux kernel, such as with AppArmor or SELinux, allows for application-level access controls even beyond user accounts. Both work to confine programs so even if exploited, an attacker's invasion is contained. SELinux tends to offer stronger isolation but a steeper learning curve, while AppArmor provides simplified profile-based controls.
You can also harden the kernel directly by disabling unneeded functionality. For example, if no external devices will plug into a server, USB and Thunderbolt ports can be completely deactivated in kernel configuration to close off an attack vector. The Linux kernel hidden PID and kernel address space layout randomization (KASLR) options also make the operating system harder to leverage in exploitation attempts.
Securing the Linux kernel both reduces the attack surface and tightly regulates application permissions for runtime protection against malicious processes. It's one of the most in-depth ways to secure a Linux host.
Configure a Robust Firewall
All publicly accessible Linux servers absolutely need a well-configured firewall to filter network traffic and controlled incoming/outgoing connections. Firewalls form the first line of network-level defense. The common iptables and nftables are included in most distributions, while alternatives like UFW provide simplified management.
Properly restricting network access is complex and beyond the scope of a single guide. However, at minimum you should deny all incoming traffic, open only required ports, and filter by IP or subnet wherever possible. UFW or FirewallD frontends can ease configuration. Regular auditing and adjustment ensures your firewall rules match the application's true needs over time as they evolve. No server is secure without carefully crafting firewall policies.
Additional Tips for Maximum Security
A few other recommendations to superbly secure Linux include:
- Pick a robust, secure, reputable operating system for your daily use and to run your business applications.
- Adding Multifactor Authentication via solutions like Duo or YubiKey beyond just SSH keys
- Use a centralized authentication service
- Restricting SUID/SGID permissions on sensitive binaries
- Managing secure system logging via rsyslog
- Hardening system services like Apache, Nginx, MariaDB which may be publicly exposed
- Using security scanners like Lynis and aquatone to test configurations and find weaknesses
- Backing up critical systems and data, so you can easily recover from issues or failures
- Physically securing servers within a locked datacenter or server room wherever possible
- Watching for and responding rapidly to any suspicious login or traffic alerts
- Segmenting internal subnets, firewall rules, and VPN/bastion access for multi-layered defense
- Ongoing security awareness training so users spot and report any signs of compromise
- Following security mailing lists to stay up with current threats and mitigation strategies
- Set up an Intrusion detection system and detect listening network ports
Ultimately, No single solution provides complete protection, requiring an in-depth defence-in-depth approach. However, taking even a subset of recommended steps ensures your Linux systems offer robust, proactive security suitable for critical infrastructure use cases.