
Cybersecurity is one of the fastest-growing and most in-demand fields today. With high salaries, ample job opportunities, and exciting work protecting organizations from digital threats, it's no wonder many are interested in starting a career in this industry.
But transitioning into cybersecurity, especially with no prior experience, can seem daunting. Required skills span a broad range, from programming to risk analysis to hacking. Fortunately, with the right strategy and effort, breaking into cybersecurity is very achievable.
Interestingly enough, this is one field I have seen people transitioning into, from helpdesk roles (A good one for launching your career in IT), software engineers, Electrical engineers, business analysts, and even Medical Doctors. (Yes, a professional medical doctor.)
It is however to note that while it is possible to make lots of money in the cybersecurity industry, that should not be your end goal, at least not at the beginning. My line manager always tells me that if there is any day I wake up and I don't feel like working in this field anymore, then I should let him know because I will create a mess rather than help, and I see his point.
Why Cybersecurity? Understanding the Field
Cybersecurity, or as others call it, Information Security, refers to protecting internet-connected systems, including hardware, software, networks, and data, from digital attacks. Cybersecurity even goes as far as Operational Technology, OT. OT is the practice of using hardware and software to control industrial equipment, and it primarily interacts with the physical world. A good example of OT is industrial control systems (ICSs) like programmable logic controllers (PLCs), distributed control systems (DCSs), and supervisory control and data acquisition (SCADA) systems. The goal is to create a security posture that prevents unauthorized access and safeguards sensitive information and systems.
Professionals in this field use tools and knowledge of vulnerabilities to defend organizations across sectors like finance, healthcare, retail, government, and more against ever-evolving cyber threats. Cyberattacks are growing in frequency, scale, and sophistication. High-profile data breaches make headlines far too often. No wonder interest in cybersecurity continues to explode.
Here are a few key stats on the state of cybersecurity today:
- Cybercrime damages are predicted to hit $8 trillion annually by 2023.
- There have been 694 publicly reported data compromises in 2023 as of July 2023.
- The global cybersecurity market size is projected to grow from USD 182.86 billion in 2023 to reach USD 314.28 billion by 2028, growing at a CAGR of 11.44% during the forecast period.
- There were 663,434 cybersecurity job openings in Q3 2023 across the United States.
This confluence of factors - escalating threats, limited security resources, and valuable data requiring protection - is fueling massive demand for cybersecurity professionals. Companies urgently need employees who can design, implement, and manage security solutions.
Starting a career in this field provides the opportunity to combat cybercrime while benefiting from high pay, abundant jobs, and reliable job security. The varied roles and career development paths make cybersecurity an exciting field to grow in.
Choosing a Cybersecurity Career Path
Cybersecurity encompasses diverse responsibilities, skillsets, and positions. Before jumping in, it helps to narrow your interests to target the right path and roles. However, at the start, it is recommended to gain as much understanding as possible in all the domains before niching out to a specific domain.
There are countless roles in cybersecurity. However, some of the job functions are shared across some roles and you will most likely find yourself doing tasks across different roles. Though specific job titles and responsibilities vary between organizations, these are five common cybersecurity career paths to consider:
1. Security Operations
Key Responsibilities: Continuous monitoring, early threat detection, incident response, forensic investigations
Common Job Titles: Security analyst, SOC analyst, cyber threat analyst
This career path focuses on daily security operations. Analysts in operations centers (SOCs) use monitoring and analysis software to identify potential incidents and anomalies. When threats emerge, they investigate and respond to contain damage and restore normal operations.
2. Network & Cloud Security Architecture
Key Responsibilities: Design and implement security tools and infrastructure, manage firewalls and VPNs, cloud security
Common Job Titles: Network security engineer, security architect, cloud security engineer
Security architects and engineers oversee technology defenses like VPNs, firewalls, and access controls. They design, build, test, and manage an organization's entire security architecture. Specializing in cloud security architecture is an in-demand skill set in 2023.
3. Application & Product Security
Key Responsibilities: Ensure security of applications, systems, and products throughout the software development lifecycle
Common Job Titles: Application security engineer, product security engineer, DevSecOps engineer
The rise of apps and connected products expands the attack surface. Application security experts work with developers to build security into software. They scan for vulnerabilities, recommend remediation, and implement application defenses.
4. Risk Assessment & Compliance
Key Responsibilities: Identify risks, determine potential impacts, and ensure compliance with regulations
Common Job Titles: Risk analyst, compliance officer, auditor
Risk assessment involves analyzing vulnerabilities and evaluating the likelihood and impact of threats materializing. Compliance officers ensure adherence to security standards and regulations. Both functions are crucial for effective enterprise security. With these roles comes a lot of reading and understanding of the industry standards, e.g. ISO, PCI DSS, NIST, CONOLT, CIS, just to name a few.
5. Security Testing & Penetration Testing
Key Responsibilities: Simulate attacks against systems and networks to uncover weaknesses before criminals do
Common Job Titles: Penetration tester/ethical hacker, security tester, vulnerability assessor
This is the role that comes to mind for most people when they hear the term Cybersecurity. Also known as ethical hacking, pen testing involves authorized professionals trying to break into systems and networks using tools and techniques similar to real attackers. The goal is to fix vulnerabilities before they're criminally exploited.
Building Essential Skills for a Cybersecurity Career
Succeeding in any cybersecurity role requires a diverse mix of hard and soft skills. Technical expertise is crucial, but communication abilities, business acumen, and other "soft" skills differentiate top performers.
When starting out, focus on developing this well-rounded foundation of essential cybersecurity skills:
Technical Skills
Networking fundamentals
This involves an In-depth understanding of protocols, switching, routing, and VPNs. Networking skills are crucial to a successful cybersecurity career and I couldn't emphasize more. Get the basics right and then build from there. Certifications help, but even better are the hands-on labs freely available on the internet. Use them.
Here are a few suggested courses for you:

Programming
As controversial as this may sound, Programming gives you an advantage when it comes to cybersecurity. Can you do without? Yes, to some extent. Is it recommended? ABSOLUTELY!
Pick one language and master it, before going on to the next. It reduces the time you will spend learning and also makes it easy to transition to the next.
The language of your choosing might not matter much. However, I would recommend you start out with Python and then Golang. The reason is that Python has been extensively used in tooling and the recent trend has seen security researchers choosing Golang because of its powerful multithreading capabilities.
Regardless of the language you choose, make sure you are making progress. Something worth noting is that you don't have to be an expert before moving to the next stage. Get the basics right, build a project or two and once you are comfortable, you can start applying that. The language you choose should be determined by the career path you want to take
OS administration
This is an area that is often forgotten by most individuals. You need to understand how an OS works. from filesystems, networking, boot process, etc., whether Windows, Linux, or MAC. For the Windows OS, go beyond the simple clicking of icons and understand how the OS actually works. Here are a few courses to get you started:

Linux on the other hand is at the heart of cybersecurity. Most security technologies and tools run well on some version of Linux and so understanding Linux is inevitable. A good resource for getting the basics of Linux right is The Linux Foundation in their Introduction to Linux Course. Once you have the basic rights, feel free to take the more advanced courses like The Linux systems administrator course by the Linux Foundation.

Cloud platforms
While this might be optional at the start of your career, understanding cloud computing gives you an edge over the rest. We have seen a growth in the adoption of cloud computing worldwide and this can only mean more demand for cloud security professionals.
I recommend mastering one cloud platform first before moving to the rest. Since most of the cloud computing platforms share lots of functionality under the hood, making a switch is usually easier.
Analysis & Assessment
Risk management
Identifying, evaluating, and mitigating cyber risks. Analysts must evaluate the impact and likelihood of threats exploiting vulnerabilities to inform mitigation efforts. This includes deciding where to focus monitoring and control efforts, as well as regular assessments to incorporate evolving threats.
Data analysis
Collecting, processing, analyzing, and interpreting security data. Detecting compromises or attacks requires collecting, processing, and analyzing security data from multiple internal and external sources. Trend analysis over time allows analysts to detect subtle indicator changes that may be missed otherwise.
Threat intelligence
Researching and understanding the latest tactics, tools, and procedures of threat actors. Ahead-of-the-curve threat intelligence involves human research tracking cybercriminal groups and state-sponsored hackers. Deploying up-to-date intelligence enables more accurate detection and response capabilities, as well as effective defenses against sophisticated, targeted modern threats facing organizations. Strong analysis and assessment overall are fundamental to a robust cybersecurity program.
Testing & Auditing
Vulnerability assessment
Not to be confused with penetration testing, VA majorly involves using automated scanners to Identify vulnerabilities in systems and applications. Familiarize with vulnerability scanners recommended by industry experts, such as Tenable Nessus, Nexpose, and even open source solutions like OpenVAS.
Penetration testing
If you love doing the "real hacking", then you have to get hands-on with this one. While it looks fancy, pentesting is usually a combination of skills from several domains, understanding how systems actually work, and then trying to break them. Enroll for the Practical Ethical Hacking Course by TCM. There is a free version of the course that was posted on YouTube. Feel free to check it out.
Compliance auditing
Assessing and reporting on adherence to policies, regulations, and controls is a key part of compliance auditing. Analysts ensure an organization's security program and technical safeguards align with internal guidelines and external rules. Audits evaluate compliance across areas like network infrastructure, access controls, encryption use, incident response, data handling, and more.
Incident Response
Digital forensics
digital forensics professionals use specialized tools and their technical skills to pick apart impacted systems, servers, and digital evidence like logs to piece together the chain of events during a security incident. This process of reconstruction and analysis is crucial for uncovering how and what systems were compromised so organizations can strengthen their defenses
Malware analysis
Dissecting and reverse-engineering malware like viruses, ransomware, and spyware. This may involve utilizing debuggers and network analyzers to understand how viruses, ransomware, or other types of malware operate and infect systems.
Disaster recovery
Not all incidents can be prevented, so planning how to recover is paramount. Disaster recovery specialists craft policies and blueprints for how organizations can restore critical services, systems, and data after major security events that cause outages, such as ransomware attacks. Their roles involve regularly testing recovery plans and ensuring teams are prepared to spring into action during real emergencies and bring impacted operations back online smoothly.
Communication & Collaboration
Technical writing
This one I can guarantee. You will write reports, lots of them, and to different people... from board members, who sometimes know little about security to the IT guys, who you will rub shoulders with just because of security. Creating reports, documentation, policies, and procedures
In most of the roles, you will also be required to do some form of documentation, so technical writing will be really important at this point. Managerial position and risk assessment positions will also require drafting lots of policies for your organization and this skill will come in handy.
Presentation skills
Cybersecurity also involves developing and delivering briefings to leadership and business stakeholders since most of the work you do will affect the business, just like any other role. So you need to develop your presentation skills, not just to technical people who understand a lot of your jargon but to nontechnical people as well, because they will be consumers of your reports, policies, and documentation.
Collaboration
Work gets done faster when people work as a team and this is still the case when it comes to cybersecurity. People are skilled differently and when they come together, solutions to problems start to come.
Even for introverts, collaboration is a skill that can be learned. Force yourself to speak to people, when necessary of course, and understand the individual personalities of your team members. This makes the process much easier and will help you to avoid brushing shoulders with your colleagues.
Collaboration also presents an opportunity for networking, especially with those outside your organization. It is also a great opportunity to develop your technical skills, technical writing, and even presentation skills.
Getting Started: Education and Certifications
There are many paths to gaining that initial base of cybersecurity knowledge. A college degree, specialized certifications, hands-on training programs, and self-study through online resources can all work.
The right starting point depends on your existing background, availability for full-time education, and financial resources. Here are the pros and cons of common options for getting started:
Bachelor's Degree in Cybersecurity or Computer Science
Pros
- Broad foundation covering all essential domains. I can't stress how much having a good foundation in IT comes in handy, especially in cybersecurity. So if you have the time, the money, and the energy, then a degree would be a good option. Be sure to choose a good university though, not one that will waste your time.
- Develops well-rounded thinking and problem-solving abilities. Due to the nature of the course content and activities in a fully-fledged university degree, you get a chance to solve lots of problems.
- Campus resources like career centers, recruiting, and research opportunities. Good universities usually have such resources where you can plug in and gain a skill or two. Join the small groups of like-minded individuals. If your university has partnerships with vendors in the tech industry, you can utilize that opportunity as well.
- Checks degree requirement box for many employers. This comes in handy when it comes to landing your first job. Some HRs just don't care about your skill until they can see that degree.
Cons
- Time commitment - full-time for approximately 4 years. This is a big one, especially for those who already have an existing degree or the 4 years is just too much at the point they are in in their careers.
- Significant financial investment - Of course doing a four-year course in a reputable university, means you need the financial muscle. Luckily, some universities do offer scholarships. Do check them out.
- General education may lack specialization -- You might lose focus along the way because of too many things. Especially when other IT roles start seeming lucrative.
Associate's Degree in Cybersecurity
Pros
- Time Commitment - An associate's degree typically takes 2 years to complete part-time or full-time, making it faster than a 4-year bachelor's program. This shorter time frame helps you enter the workforce quickly.
- Cost-Effectiveness - Community colleges tend to be more affordable than 4-year universities. An associate's degree allows you to learn valuable skills without as much financial burden as a bachelor's.
- Specialized Content - As a 2-year program focused solely on cybersecurity, the coursework will provide more hands-on technical skills compared to a general computer science bachelor's degree. You'll learn core security concepts.
- Industry-Recognized - Many employers are open to hiring associate's degree holders, especially for entry-level security analyst, network support, and systems administration roles.
Cons
- Limited Career Progression - While an associate provides a solid cybersecurity foundation, it may cap further career growth potential compared to a 4-year degree. Roles like management, and architecture design may require a bachelor's minimum.
- Less technical depth - Bachelor's programs delve deeper into various technical areas like programming, operating systems, networking, etc. An Associate's provides a broad overview.
- Possible need to continue education - To advance beyond entry-level roles over time, you may need to pursue further education like bachelor's completion programs part-time while working.
Cybersecurity Bootcamps and Certification Programs
Pros
- Develop job-ready skills in as little as 3-6 months - Most programs are intense, full-time studies that can be completed in 3-6 months. This timeline gets new qualifications much sooner than traditional 4-year degrees or associate degrees
- Lower costs than college degrees and associate - Tuition for intensive programs is significantly cheaper than college. Some even offer financing. This lowers barriers for those wanting to transition careers affordably.
- Specialized, practical education geared towards day-1 job skills - Curricula focus entirely on applying tools and techniques used daily in roles like threat analysis, network security, and penetration testing through simulated work scenarios. Some programs even include internships or apprenticeships, allowing graduates to gain work samples before fully entering the job market.
Cons
- No credential granted - completion certificates only - Students only receive a completion certificate, rather than an Associate or Bachelor's degree. This can potentially limit career advancement opportunities later on.
- Very narrowed focus - lack of general education - The intensive and accelerated nature means programs have a very narrow technical focus, teaching specific skills but lacking broader general education. You might end up missing out on learning other valuable skills like communication, critical thinking, and business acumen. But of course, if you have experience in other fields, this can be taken care of.
- Quality varies greatly between programs - With no standardization or accreditation, the quality of instruction and career support can vary significantly between different boot camps and certification providers.
Self-Study Through Online Resources
Pros
- Extremely flexible and self-paced - This is the biggest flex of this mode of study. Determining your own schedule and learning path provides the ultimate flexibility. With many free online courses, videos, books, and other resources, it also allows you to gain skills at little to no monetary cost.
- Learn while working or supplementing other education - Self-study permits learning new skills while keeping your current job. It serves as a way to supplement other education or explore cybersecurity as a potential career change.
Cons
- No guided curriculum or formal credential upon completion - Without the routine of courses, assignments, and exams, it can be easy to lose focus or motivation over time. It requires strong self-discipline to properly utilize self-paced learning. Upon completion, there is no recognized certificate or diploma to validate your new skills and knowledge for employers. Additional certifications would still need to be obtained.
- Difficult to determine the hiring value of self-education - It may be difficult to demonstrate the depth and applicability of your self-study to potential hiring managers without formal assessments or recommendations from an established program.
Entry-Level Cybersecurity Certifications
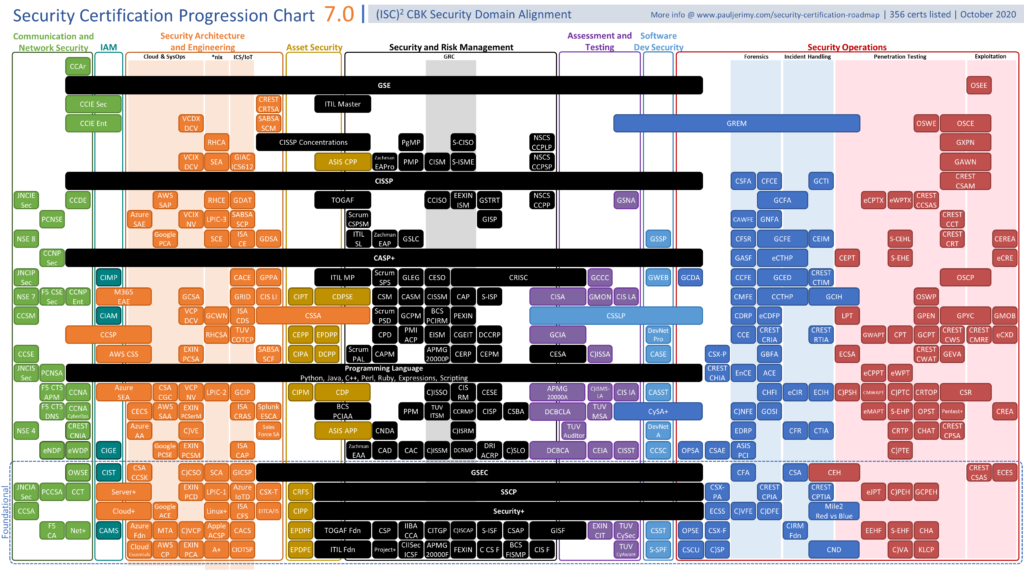
Industry certifications offer another path to learning foundational skills and demonstrating credibility to employers. While there are so many debates about certifications, they do come in handy, especially in cyberspace. While they might help you get through the HR to the interview panel, they do offer more than that, especially the practical certifications. There are so many guides about which certifications but here is a guide that summarizes them well.
Get the certification roadmap and picture.
Here are a few recommended entry-level certs.
CompTIA Security+ - Covers core skills for IT security roles like compliance, threats, vulnerabilities, access controls, cryptography, and risk management.
CompTIA CySA+ - Focuses on IT security analytics and hands-on cybersecurity tools for SOC roles.
CompTIA PenTest+ - Validates knowledge and skills for penetration testing and vulnerability assessment.
The right starting point depends on your existing skills, availability, financial resources, and interests in cybersecurity. A combination of education and certifications builds a solid foundation of in-demand abilities.
Gaining Invaluable Experience
Beyond formal education, real-world cybersecurity experience is essential for a successful career. Hands-on experience proves skills and teaches nuances that no classroom can. Here are impactful ways to start gaining that critical experience:
1. Setup a Home Lab
A home lab environment provides the perfect sandbox to experiment with tools, systems, and techniques actually used by security professionals. Typical home lab setups involve:
- Virtualization software like VirtualBox or VMware on a desktop/laptop. If you have the financial muscle, you can get a server on Amazon or eBay, or elsewhere and start playing around with virtualization platforms like ProxMox, ESXi, or OpenStack. Be sure to pick one and be good at it before moving on to the next one.
- Cloud platforms like AWS, Azure, or GCP provide on-demand VMs. The good thing about cloud platforms is that they also have certifications. So the hands-on labs can be a good way of preparing for those certs.
- Old enterprise hardware turned into servers running VMs
- Raspberry Pi devices to simulate IoT systems if you are into IoT security. (A lucrative one BTW)
Home labs allow safely trying out activities like:
- Build an Active Directory forest: Create an Active Directory domain to learn how domains, trusts, OUs, and GPOs work. Manage users, computers, and permissions.
- Run DNS/DHCP from AD: Integrate internal DNS and DHCP services with AD for centralized management. Learn how DNS records and DHCP scopes work.
- Multiple network zones: Set up different security zones like internal network, DMZ, and VPN zone. Configure routing and firewall policies between zones.
- Install and configure a firewall: Use FortiGate or other enterprise firewalls to build deeper networking and security skills. Learn routing, NAT, ACLs, and VPN configurations.
- Web server on Windows/Linux: Deploy websites on IIS or Apache/Nginx. Configure HTTPS, authentication, and permissions. Understand attack surfaces.
- WordPress blog on Linux: Self-host a blog and learn content management best practices. Hardening, plugins, backups.
- Kali Linux: Regularly use security tools for scanning, brute forcing, hashes, and forensic investigations to build hands-on security skills.
- OpenBSD DNS server: Deploy a DNS server using more secure OpenBSD and DJBDNS to learn alternative implementations.
- Proxy server: Set up a transparent or anonymous proxy for traffic filtering and monitoring.
- Self-hosted VPN: Use a VPS and build your own VPN server for secure remote access.
- Email server: Set up email infrastructure using Postfix/Exim/Sendmail. Anti-spam, encryption, DKIM/DMARC.
- Virtual networks: Simulate networks, deploy vulnerable VMs, and practice penetration testing, firewall rule testing, and incident response.
- Malware analysis: Perform static and dynamic analysis on malware samples to understand techniques.
The goal is to continually build and evolve the home lab infrastructure for hands-on learning of networking, operating systems, and security controls. You don't have to do all these to become a cybersecurity engineer but most professionals do these things daily, whether in their line of duty or as a way of enhancing your skills.
2. Contribute to Open Source Security Projects
The cybersecurity community maintains many open-source tools and platforms. Contributing provides a great experience while giving back and building a network. Ways to contribute include:
Finding and reporting bugs - Testing software and responsibly disclosing flaws helps improve security for everyone. This is where bug bounty comes in. Imagine getting paid for finding bugs while at the same time building your portfolio!
Suggesting new features - Proposing and discussing enhancements to existing open-source tools. Start with the tools you use every day. Of course, there are improvements that can be made. Suggest them. Even better, Suggest how to implement, and if possible, deliver the solution.
Writing and improving documentation - A major need since developers rarely enjoy writing docs for users. This will also build your documentation skills when you land your first job.
Submitting code through pull requests - Open source allows contributing code fixes or full new features.
GitHub is a great platform to search for cybersecurity projects seeking assistance across those areas.
3. Compete in Cybersecurity Competitions
Events, like capture the flag (CTF) competitions, offer a fun way to practice technical skills in a gamified setting. Large conferences often host associated CTFs. There are also many online CTF sites to join, such as:
- HackTheBox - Hosts CTFs with various challenge levels requiring different skills to "hack" and earn points.
- Root-Me - Hundreds of hacking challenges across categories like forensics, cryptography, web exploitation, and more.
- PicoCTF - Free computer security game targeted at middle and high school students.
- US CyberPatriot - Youth cyber education program featuring national defense-themed competitions.
- Tryhackme
4. Earn Relevant Industry Certifications
We already covered entry-level cybersecurity certifications. However, more advanced certifications that align with your chosen specialization also provide a big boost. Be sure to check the Security certification roadmap guide for in-depth recommendations.
5. Perform Internships and Apprenticeships
Internships provide supervised work experience and networking opportunities. Cybersecurity students can search sites like LinkedIn, Chegg, and individual company sites for internship listings. Don't focus on the money at first.
Building Projects to Showcase Skills
Cybersecurity hiring managers don't just want to see education and certifications. They want to see demonstrated ability to apply skills through relevant projects and activities. Projects also demonstrate passion, a key factor when it comes to cybersecurity roles. Here are examples of worthwhile cybersecurity projects to build your portfolio:
- Write security tools or scripts - Automate tedious tasks or implement a new capability. Great for demonstrating programming skills.
- Find and report bugs - First, get permission, then probe systems and write polished reports summarizing findings and remediation advice. Join bug bounty programs like HackerOne, Intigriti, and Bugcrowd and create a public profile that you can show to employers. Competition is tough though!
- Design and configure a secure network - Document architecture, protocols, firewall rules, and other details to exhibit comprehension. Blog posts are a nice way of doing it. Hence this blog!
- Record educational videos - Create tutorials explaining cybersecurity concepts or how to use specific tools. Great for cementing knowledge while producing content.
Establishing an Online Presence
Building an online presence in cybersecurity is important for career growth and skill development. A good first step is setting up a professional LinkedIn profile and optimizing it with your relevant experience, skills, and qualifications. LinkedIn should be prioritized as it is primarily used for professional networking and is actively used by recruiters. While engaging on platforms like Twitter can also be beneficial, it's not necessary to be active on every social media channel. Focusing engagement on two platforms, such as LinkedIn and a company blog, provides an effective online presence.
Once active profiles are established, regularly contribute useful, industry-related content. Posting about technical concepts, personal projects, or news articles demonstrates expertise. Sharing these posts sparks discussion and increases visibility to other professionals. Interacting with colleagues and leaders through comments or messages also expands your network over time. As connections grow, opportunities for new partnerships or referrals may arise. Consistency is important—only through continuous quality contributions will your online brand be recognized.
Many cybersecurity forums and groups exist on platforms like Reddit and Discord. Join communities aligned with your interests to exchange ideas and network with peers. Contribute advice and insights where possible. Don't be caught up in these and be sure to watch out for Imposter Syndrome!
Attending Cybersecurity Conferences
Industry conferences provide unparalleled opportunities to learn, network, and raise your profile. Make attending relevant cybersecurity cons a priority early on. Conferences allow you to directly connect with professionals working at all levels in both large organizations and small startups. Start local, participate, and try to give your own talks as soon as you’re ready. So why attend them?
Networking Opportunities
One of the biggest advantages of conferences is the ability to meet and connect directly with cybersecurity professionals face-to-face. Take full advantage of networking sessions, speaker Q&As, and lunches/dinners to introduce yourself and exchange contact details with people working in roles you aspire to. Follow up after the event on LinkedIn to continue conversations. You never know when your new contacts may be able to help with a job lead, advice on your resume, or an introduction within their company.
Learning the Latest Trends
Conferences allow you to learn directly from high-profile speakers and vendors about the newest threats, regulations, technologies, and strategies companies are using to defend themselves. Attend sessions outside your specialty to expand your knowledge base. Take thorough notes that you can refer back to later.
Exposure to Potential Employers
Many large cybersecurity vendors and consultancies exhibit and recruit at major conferences, providing a chance to showcase your skills and stand out. Have your one-minute elevator pitch prepared and resumes on hand to distribute. Consider volunteering as well to gain face time with company representatives. Don't underestimate the small connections that could turn into job opportunities down the line.
There are countless conferences held each year both in-person and virtually. Use sponsorship opportunities, student discounts, and location to determine the optimal events for advancing your career goals in cybersecurity. Consistently participating is key—you never know when the right contact will be made.
Find a Mentor
Mentorship can be tremendously beneficial as you work to enter and progress in the cybersecurity field. Experienced professionals can offer guidance to help navigate obstacles, expand your learning, and take advantage of opportunities.
Ideally, seek out multiple mentors over time who can fill different needs as you grow. Look for individuals whose backgrounds and accomplishments closely align with your own goals. Follow potential mentors online to get a sense of their character, work ethic, and expertise.
Once you've identified suitable candidates, prepare thoroughly before making initial contact. Demonstrate through your own independent study and hands-on projects that you're motivated and have laid a solid foundation. Mentors want to foster self-starters, not give remedial assistance.
When reaching out, keep introductory messages concise yet personable. Emphasize what attracts you to their specific experience and how they can support your ongoing learning. Suggest an initial informational call at their convenience rather than immediately asking for time commitments.
Express sincere gratitude for any guidance provided, regardless of whether a long-term arrangement forms. Maintain respectful communication and highlight achievements that resulted from their influence. Over time, look for opportunities to pay their mentorship forward to others just starting out.
It is important to understand that mentorship is not a one-way street. While experienced professionals are often willing to share their time and knowledge, they want to invest in individuals who are self-motivated learners. The bulk of the effort will fall on you as the mentee. Coming to mentors with well-thought-out questions after preliminary preparation will earn their respect.
Starting the Job Search
At some point, you'll be ready to actively start applying and interviewing for that first full-time cybersecurity role. Here are job search tips tailored for aspiring cybersecurity professionals:
Highlight Relevant Skills and Experience
Since cybersecurity job requirements vary, precisely tailor your resume to each role. Beyond required certifications, emphasize skills and experience most relevant to that position. Quantify achievements with numbers when possible.
Leverage Your Connections
Network at conferences and through your online presence. Reach out to connections about opportunities and ask to be referred when possible. Referrals get much more attention.
Research and Practice Interviewing
Understand the company, role, and industry trends to ace interviews. Prepare responses demonstrating required hard and soft skills. Research common cybersecurity interview questions and practice answering them fluidly.
Join Cybersecurity Job Sites
Beyond general sites like Indeed and LinkedIn, specialized cybersecurity job boards exist such as WorkCyber, CybersecurityJobsite, and CybersecJobs. Follow their social media accounts to hear of new openings.
Highlight Passion and Curiosity
Hiring managers value passion and continual learning. Convey your drive to protect organizations from threats and genuine excitement for constantly evolving security work.
Growing Your Career Over the Long Term
Starting that first role is a major milestone. But cybersecurity offers many avenues to evolve your career over years and decades. Here is a 5-step framework for maximizing long-term career development and progression in cybersecurity:
1. Specialize in a Domain
Early on, identify and specialize in a cybersecurity domain that interests you - for example, cloud security, application security, threat intelligence, or digital forensics. Pursue advanced certifications, education, and projects within your specialty. Become a go-to expert.
2. Understand Business Needs
Cybersecurity supports larger business objectives - it does not operate in a vacuum. Learn to quantify cyber risks in business terms and communicate security priorities in the context of organizational needs.
3. Develop Soft Skills
Well-rounded "soft skills" like communication, collaboration, creativity, and presentation abilities differentiate average from exceptional performers. Especially important for higher management roles.
4. Cultivate Mentor Relationships
Seek both peer and senior mentors who can provide career guidance, industry introductions, and unvarnished feedback. Give back by mentoring newcomers to the field.
5. Network Strategically
Attend conferences, volunteer for industry groups, speak at events and connect thoughtfully on social media. But focus on quality over quantity interactions that build genuine relationships.
Conclusion
Launching a successful and rewarding cybersecurity career takes research, planning, and persistence. But the effort is well worth it. The expertise of cybersecurity professionals will only grow in importance and demand. Roles span diverse specialties from ethical hacking to security engineering - there are options for every interest.
Use this guide's steps to educate yourself, gain experience, build projects, network with peers, and strategically market your abilities. Before you know it, you'll land that first role and be building a bright future defending the digital world from ever-present threats.




