
Mass surveillance capabilities allow both governmental agencies and private corporations to monitor the activities, communications and locations of citizens to an unprecedented degree. Interconnected technologies have enabled ubiquitous data collection, analysis and retention on entire populations without their consent. This represents a dangerous erosion of civil liberties and personal autonomy.
However, mechanisms for resistance exist, if one understands the underlying technical infrastructure enabling such intrusions. Two robust techniques available today,Virtual Private Networks (VPNs) and de-Googled mobile phone operating systems are a few steps in the right direction towards countering digital surveillance overreach .
Who Is Conducting Surveillance and Why
Before jumping into solutions, we need to understand how extensive surveillance is being done and the motivations.
Government Surveillance
The most obvious driver of digital surveillance is government intelligence agencies. Thanks to whistleblowers like Edward Snowden, we now know the stunning extent to which groups like the NSA, FBI, and CIA spy on digital communications and activities within the US and abroad.
From phone records to emails to web browsing, government agencies justify mass surveillance as necessary to combat terrorism and other crimes. However, critics argue these practices undermine civil liberties while doing little to enhance actual security.
For instance, governments are able to conduct surveillance through:
- Direct access to servers and infrastructure of phone companies and Big Tech firms
- Hacking tools that break encryption
- Mandatory data sharing policies for tech companies
- Purchase of user data from brokers
- Advanced tracking mechanisms like facial recognition cameras
In addition to electronic surveillance, governments can physically identify citizens through documentation like driver’s licenses and medical records. When combined with footage from widespread CCTV cameras, physical surveillance can also pose privacy issues.
Countering government mass surveillance is extremely difficult thanks to the state’s unique powers and resources. But citizens can take steps to reduce their digital footprint and make surveillance more difficult, which I will cover shortly.
Corporate Surveillance
In addition to government activities, private corporations conduct their own mass surveillance by compiling extensive profiles of user behaviors, interests, locations, and more. This data enables companies to better target advertising - their primary source of revenue.
Google and Facebook may be the biggest offenders when it comes to corporate surveillance, but many mobile apps and websites also collect user data aggressively.
Some types of corporate surveillance include:
- Recording locations through phone sensors and apps
- Placing trackers on websites to follow browsing habits
- Analyzing writing samples, searches, posts to determine interests and habits
- Purchasing data from brokers who trade in user information
- Requiring personal info to sign up for accounts and services
Fortunately, individuals have more direct power to thwart corporate surveillance through their choices. You cannot directly stop the NSA from spying, but you can prevent Google and Facebook from tracking you with greater ease.
Surveillance Capitalism
The business model that drives companies like Google and Facebook is called surveillance capitalism. Under this model, corporations derive enormous profits from mass surveillance used to fuel advertising systems. Users pay for services like search and social media by handing over their personal data.
Surveillance capitalism poses inherent risks to user privacy and autonomy. When entire industries operate by maximizing data collection and analysis, individual rights erode dramatically.
Furthermore, the rise of surveillance capitalism has closely aligned private Big Tech firms with government interests in keeping tabs on citizens through their digital activities. Corporations may not directly conduct state surveillance, but they have created an infrastructure perfect for government agencies to tap into.
Understanding the dominance of surveillance capitalism today is key to recognizing the stakes around corporate tracking. Google and others have built multi-billion dollar empires based on erosion of privacy - they will not change easily. Thus we as individuals must take direct responsibility through self-defense measures.
Thankfully, we can improve our privacy by taking a few measures, two of which will be discussed in the following sections:
Technique #1: Use a VPN
A Virtual Private Network (VPN) is one of the most powerful tools available today for everyday citizens to guard privacy in the digital sphere.
VPNs provide two core benefits: hiding your real IP address and encrypting traffic between your devices and the internet, preventing surveillance and hacking. I understand there are arguments that you can still achieve encryption by using SSL/TLS whic is used by default in the HTTPS protocol, which is actually true, but as you will see, the problem is in the way the TLS encryption is implemented, which allows for surveillance even when your traffic is encrypted.
How VPNs Work
When you connect to the internet, your internet service provider (ISP) assigns devices an identifying IP address like 104.245.124.1. This address marks all your traffic as coming from you specifically.
Websites, governments, hackers - anyone can monitor this IP address to follow your digital movements across the web and build profiles.
A VPN provides an encrypted tunnel between your devices and the open internet, hiding your home IP address:
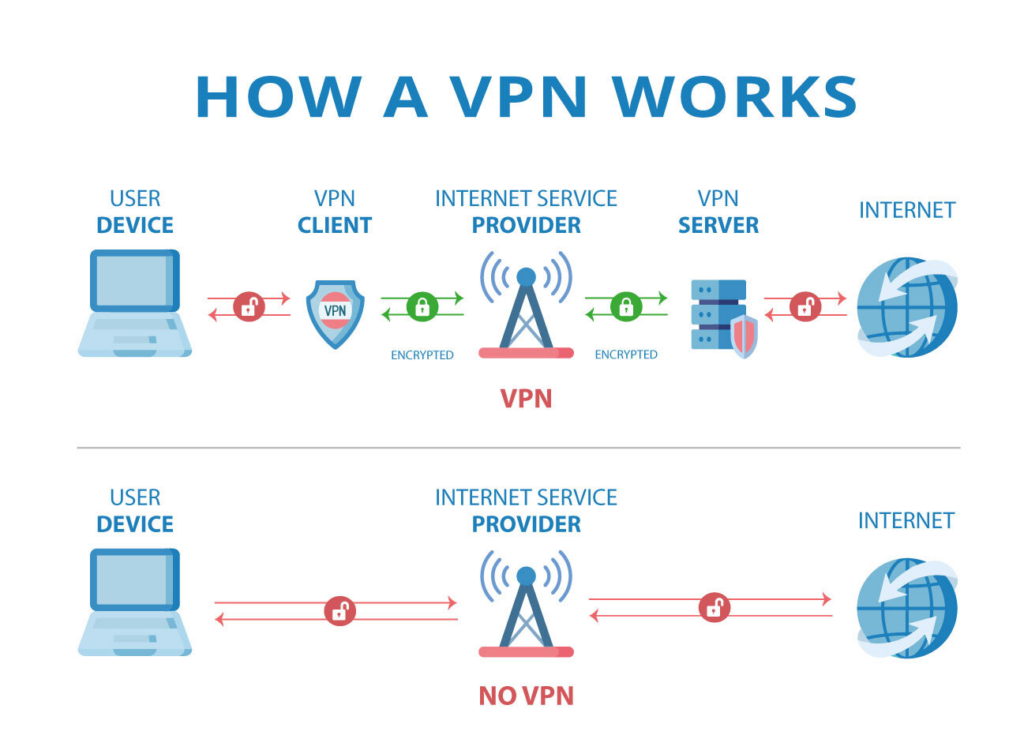
Instead of connecting directly with your home IP, your traffic enters a VPN server. This server has its own IP address shared by potentially thousands of other VPN users.
So when you visit a website, it records the VPN server's IP instead of your personal one, anonymizing you. It cannot distinguish your device from anyone else connected to that server.
Furthermore, the encrypted VPN tunnel prevents outside parties like your ISP from surveilling your activity as data passes through. They see only gibberish, not your actual browsing, watching, messaging, etc.
This combination of hiding IP + encrypting traffic provides powerful protections against digital tracking.
Why VPN Encryption Defeats Surveillance
You might wonder - can't governments or hackers simply crack the VPN encryption to reveal identities and traffic? After all, most web traffic utilizes HTTPS encryption which is not unbreakable and with the way the TLS encryption is implemented, it allows for surveillance even when your traffic is encrypted.
Here is a key technical detail about how VPN encryption differs:
Modern web encryption relies on a system of trust called Certificate Authorities (CA). When you connect to a web server, the server provides a digital certificate to authenticate itself as legitimate.
Your device checks this certificate against CA records which confirm the server is who it claims. Traffic can then be encrypted between device and server to prevent eavesdropping.
However, a major weakness is that surveillance agencies can coerce CA themselves to issue fake certificates impersonating real servers. Moreover the problem is in the way the TLS encryption is implemented, which allows for surveillance even when your traffic is encrypted.
Most surveillance agencies install themselves as CA on your device and so they can verify fake certificates as well as decrypt SSL certificate as explained by Rob Braxman in this Video.

For example, a spy agency could generate a cert falsely claiming to be Google.com. Your device sees this fraudulent cert validated by a CA and believes it to be authentic.
An surveillance agency with a fake but CA-approved cert can now secretly intercept web traffic by impersonating the server you wish to visit. This is known as a "man-in-the-middle-attack” (MITM) and allows decoding of the encrypted session through the phony cert. Governments utilize MITM frequently by compromising Certificate Authorities.
However, the encryption used in VPN tunnels is different and much more resistant to tampering:
- VPNs use certificate pinning rather than trust chains - Certificates are pre-shared between client and server rather than dynamically checked against a central authority. This prevents root certificates controlled by a third party from being inserted.
- Many VPNs use OpenVPN software which utilizes OpenSSL libraries that are open source and publicly audited rather than proprietary black boxes. The encryption algorithms are robust.
- VPN traffic is concentrated through a small number of servers rather than the billions of individual web sessions across the internet. This means extra scrutiny can be paid to server security. Corporate and government intelligence agencies typically take the path of least resistance.
So while no encryption is completely unbreakable, VPN tunnels are a much harder target requiring significantly more resources to compromise. This raises the bar and places mass surveillance of VPN traffic outside the reach of most bulk collection programs.
Of course, the VPN provider itself could hypothetically observe traffic if it wished since it controls servers. But for reasons outlined later, commercial VPN companies have strong incentives not to snoop.
Additional VPN Benefits
Beyond hiding IP address and encrypting traffic, commercial VPN services provide other useful privacy benefits:
Prevent DNS Hijacking
Many VPN services use their own DNS (Domain Name System) resolvers - an address lookup allowing you to type site URLs instead of numerical IPs. This prevents your device from using a compromised DNS server controlled by your ISP or government which could redirect your traffic through spy proxies.
Ad Blocking
Popular VPN provider systems utilize technology like PiHole to block ads and trackers at the network level - preventing sites from ever loading those elements in pages you visit. This significantly curtails corporate tracking.
No Geofencing Data
Geofencing warrants allow police to request location data on all devices within a given area and time, usually from Google or Apple. VPNs hide device identifiers from ever reaching these companies, so you cannot be tracked through geofencing.
Hiding your location also prevents advertisers from using geographic targeting. You'll get generic ads rather than creepy, microtargeted ones based on your real-world movements.
Multi-Hop Servers
Advanced VPN services route traffic through multiple servers (hops) for added layers of encryption and dissociation between you and destinations. This includes exit servers in jurisdictions with strong privacy laws for additional legal protection.
No Activity Logs
VPN providers that don't keep traffic or connections logs protect you from government demands to hand over data for after-the-fact surveillance.
Choosing a Trustworthy VPN Provider
No technology is foolproof, so you must carefully vet any VPN provider you choose to ensure reliability. Here are key factors to investigate:
Independent Audits - Trusted firms should conduct regular audits of VPN code and infrastructure to certify no leaks or breaches exist. Many leading companies like ExpressVPN, NordVPN, Proton VPN, and others have published audits.
Strict No Logging Policies - VPN providers should not record any activity or connection logs that could reveal user details if compromised or seized. Audits help confirm this policy.
Location Outside Surveillance Alliances - It is risky to use VPN companies still operating within 5/9/14 Eyes jurisdictions since legal liability may compel logging. Switzerland, Panama, British Virgin Islands are safer bases.
Accepts Anonymizing Payment - Requiring personal payment details like credit cards undermines anonymity. VPN firms serious about privacy accommodate anonymous methods like gift cards or crypto.
Transparent Ownership - Providers operated openly by known individuals generally inspire more trust versus fully anonymous companies. But use judgment here.
There are three recommended VPN providers that you can check out as explained in this article

No VPN can provide 100% assurances, but taking appropriate precautions allows you to enjoy reasonable anonymity.
What About iCloud Private Relay?
You may have heard of Apple's privacy offering called iCloud Private Relay rolled out in iOS 15. At a surface level, it sounds similar to a commercial VPN - routing traffic through two proxy servers to hide IP and prevent spying.
However, there is a danger in trusting iCloud Private Relay as a substitute for a proper VPN. Cryptography experts have highlighted technical shortcomings in Apple's approach that undermine privacy versus traditional VPN encryption and tunneling protocols.
Furthermore, concentrating vast amounts of traffic through Apple's servers could actually centralize user data in ways amenable for government collection demands. I cannot recommend depending on any big tech corporation's infrastructure when alternatives like VPNs enable routing via independent providers instead. Stick to traditional VPN services for most robust privacy protections.
Government VPN Crackdowns
Given how effectively VPN technology counters surveillance, some restrictive governments like China and Saudi Arabia have attempted technology to restrict or decrypt VPN traffic flows.
Some governments may claim (loudly) to restrict VPNs for reasons like copyright enforcement or maintaining internal control rather than explicit privacy violations. But make no mistake - the ability to hide online activity is what makes authorities view VPNs as threats in the first place.
Technique #2 De-Googled Phone OS
Beyond desktop/laptop connections, mobile phones provide both governments and corporations rich new data streams to harvest through built-in sensors and apps with privilege access. iPhones and Android devices have become tracking machines as surveillance capitalism monetizes this telemetry trove.
However, by switching to an open source Android variant with Google services extracted (de-Googled), you can drastically reduce organization profiling and monitoring:
Among other benefits, degoogled phones have the following key advantages:
- No identifiers for mapping behavior to personal profiles
- Preventing passive and active location tracking
- Reduce corporate telemetry analyzed for surveillance capitalism
Combining this with practices like VPN routing and secured communication apps can help cover remaining weaknesses that persist around cellular network triangulation. Let's discuss this in detail:
Default Smartphone Operating Systems Aid Surveillance
Every iPhone and typical Android device runs an OS tightly tied to Apple / Google services frameworks:
This provides the seamless experience and abundant app selection users expect. But we pay a hidden price for such convenience through incessant, aggressive tracking built directly into the OS itself.
You cannot use an iPhone or Google Android device without apple and Google having full profiles of your interests, behaviors, friends, media consumption, purchase tendencies, location history, demographics, and more compiled from both obvious and subtle signals.
This data fuels surveillance capitalism - and remains vulnerable for governments to tap as well.
But the most dangerous aspect is how integrated surveillance occurs by default. Out of the box, iPhone and Google Android users have virtually no option to opt-out of intricate tracking and profiling without complex technical know-how. Although settings exist to toggle supposed "tracking protection", they are misleading at best or outright deception at worst.
Let's breakdown key vectors these OSes use to "phone home" (easily) identifiable user telemetry:
Associated With Official IDs
All usage ties irrevocably back to your AppleID/Google account, linking behaviors into an inescapable personal profile.
Actively Track Location
Phones transmit GPS and WiFi scan pings constantly to Apple / Google servers for analysis unless you completely disable location services (which many apps require anyway). This builds an alarmingly precise realtime and historic location map.
Passive Location Tracking
Even with location services disabled, Apple and Google ingest device telemetry through WiFi / Bluetooth / cellular connectionpassive monitoring revealing approximate positions. Truly preventing passive tracking requires radical action like software modification.
Unique Hardware IDs
Identifiers like IMEI and serial number persist as alternate tracking vectors when no logins are used. They provide just enough fingerprinting to combine other metadata like usage patterns and passive location into high fidelity behavioral profiles.
OS and First Party Apps / Services
Centralized, proprietary codebases directly phone home telemetry without user transparency or control. iOS and Google Play Services run as privileged processes impervious to blocking. Disabling them cripples functionality, demonstrating integration of surveillance into the user experience itself.
Pre-Installed Bloatware
Plenty of third party apps come included on phones as well, many collecting and transmitting their own trackers. These cannot be fully removed without advanced technical intervention.
In essence, mobile OS developers have too much incentive to maximize data collection. Participating in the Apple and Google ecosystems requires surrendering privacy by design.
Apple and Google Must Comply with Government Data Requests
While Apple and Google are public companies, the operating systems running on 99.9% of smartphones globally are either iOS or Android. This gives their developers de facto monopolistic control.
For example in the USA, tech monopolies are obliged to secretly comply with vast data sharing programs:
- The Patriot Act and other statutes enable bulk collection of mobile user data without a warrant. These laws override older privacy protections.
- Secret FISA court orders compel compliance without public accountability or even the ability to admit data is shared.
- Backdoors in mobile OS code allow deep access to personal data as revealed by Edward Snowden. E.g. the NSA's PRISM program.
Location Tracking Cannot Be Disabled
One of the most dangerous surveillance threats comes from mobile location tracking. Monitoring someone's movements provides an intimate window into their lives. We've all seen the settings on our phones that allow limiting apps that can access your location.
But what most people don't realize is that the OS itself cannot be prevented from tracking your location. The settings to disable location tracking you see only apply to third party apps, but in most cases, not the OS.
Here are a few examples of how your location is spied on:
- GPS - The raw satellite signals used for navigation and mapping also passively reveal position. No user action is required.
- A-GPS - Assisted GPS via the Google SUPL server discloses location based on nearby cell tower. Mandatory for GPS to work quickly.
- WiFi Scanning - Reveals precise indoor location by triangulating signal strength of nearby WiFi routers in database. Always-on operation.
- Bluetooth Scanning - Bluetooth beacons and device fingerprinting enable tracking worldwide. Can't be disabled.
- AirTag Scanning - Apple iPhones reveal their position whenever detecting AirTag and UltraWideBand signals. Mandatory system-level function.
And keep in mind, even if you completely power off your phone, many of the above techniques still work, especially on the iPhone.
Enter De-Googled Android OSes
However, alternatives do exist...if you are willing to forego some conveniences.
What Is De-Googled Android?
"De-Googled" Android refers to open source Android OS derivatives that scrub out closed source Google services dependencies. Google core components are replaced with free, privacy-respecting alternatives:
Popular options include LineageOS, GrapheneOS, and /e/OS. Like any othe product, there are both advantages and disadvantages:
Pros
- Open source code auditable for privacy and security
- No persistent identifiers linking back to personal profiles
- Disable location tracking completely
- Block ads and trackers via firewall
- No linkage between device identifiers like IMEI to personal identities stored in Google accounts
- WiFi scanning for indoor tracking can be disabled
- No preloaded Google apps reliant on surveillance and tracking
- Enhanced OS permission controls for sensor access
Cons
- Lose access to some proprietary apps like Google Maps (but many alternatives exist)
- Gesture and camera components may not work perfectly
- Must manually download apps outside centralized store
- Increased responsibility to configure security controls
The downsides reflect the expectations of convenience we have surrendered for surveillance capitalism access. But with some diligence, de-Googled Android provides meaningful privacy - at cost of moderate effort.
Mapping of Tracking Vectors to De-Googled Android Defenses
| Tracking Vector | De-Googled Android Defense |
|---|---|
| Associated With Official IDs | No requirement for Google account - anonymous usage |
| Actively Track Location | Toggle location permission app by app or device wide |
| Passive Location Tracking | No persistent background process owned by Google to monitor device telemetry covertly |
| Unique Hardware IDs | MAC address randomization, no serial number reporting dependencies |
| OS and 1P Apps / Services | AOSP open source means no phoning home without permission |
| Pre-Installed Bloatware | Control exactly what apps are installed - no bloat bundle required |
With Google eliminated, no single centralized profile exists to compile Cross app/service telemetry either. This represents a major structural shift from surveillance capitalism tracking norms.
Features like firewalls, permission managers, anonymous usage and MAC randomization combine to offer true opt-out controls over tracking. Default open source Android still enables efficient smartphone functionality without the privacy trade off.
However, a few gaps remain...
Residual Weaknesses
Cell Network Triangulation
Carriers still receive IMEI and IMSI identifiers allowing location tracking when cellular service activated. But this remains much coarser than GPS.
Supl.Google.com
Special GPS assisted lookup owns by Google happens on all smartphones for quick location fixes.
Additional Considerations
While VPNs and de-Googled Android phones provide robust protection against digital monitoring, there are some additional considerations worth noting:
- Government Backdoors - Determined state actors may still be able to circumvent encryption or profile users through legal or illegal means such as exploiting zero-day vulnerabilities, targeting VPN company servers directly, pressuring employees, etc. Total anonymity is very difficult.
- VPN Logs - Some VPN providers still keep some connection logs that could identify users. No-log providers are preferable, though difficult to entirely verify. International jurisdiction also plays a role in data disclosure risks.
- Third-Party Trackers - While a VPN and privacy-focused phone protect core internet activity and location, invisible third-party trackers still operate on many sites and apps. Additional browser extensions may be needed.
- De-Googling Challenges - Removing all Google dependencies is an imperfect process requiring technical knowledge. Alternative app stores and MicroG workarounds can leave some location leakage avenues. Carrier location may be unavoidable on standard networks without a SIM.
- Law Enforcement Capabilities - Local police agencies continue expanding surveillance technologies like stingrays, aerial drones and controversial facial recognition. Complete avoidance requires dedicated operational security practices beyond standard consumer technologies.
Overall, a VPN combined with prudent use of a de-Googled Android phone provides strong protections for average users against mass digital monitoring programs. These dual techniques close major avenues for data exploitation by the largest technology and intelligence entities. While not a complete solution, they help level the playing field against invisible opponent's constantly advancing their surveillance powers. With dedication and necessary tradeoffs, individual online privacy can still be meaningfully defended.
Resources for Getting Started
For readers interested in implementing the techniques discussed, here are some recommended starting points:
- /r/DeGoogle - A helpful Reddit community for advice and guides on de-Googling Android phones through custom ROMs, microG and F-Droid app alternatives.
- /r/Privacy - A wide-ranging privacy-focused subreddit covering topics beyond just Android, with lots of discussion on threat models, adversary knowledge and operational security practices.
- GrapheneOS - One of the most advanced de-Googled ROM options developed with security in mind by the Qubes OS team. Requirement of unlockable device.
- Private DNS - Apps/middleware that can help block third-party trackers and ads on a standard Android phone without root access. Not as thorough as de-Googling.




