
Have you ever accidentally mistyped the name of a website in your internet browser's address bar and ended up on the wrong site? You try to go to google.com but accidentally type three Os instead of two, or you aim for facebook.com but miss a letter. It's an easy mistake to make, but one with potentially serious consequences.
Many of these misspelled or lookalike domain names are purchased and used by threat actors, adversaries, hackers, and scammers with malicious intent. They may host credential harvesting websites to steal your username and password through phishing, deploy malware, or perpetrate other social engineering scams. What if you could get ahead of these threats by identifying typo squatted and lookalike domains before the bad actors deploy them?
Enter DNSTwist, a powerful tool that allows you to do just that. Developed elceef, DNSTwist is a domain name permutation utility for detecting homograph phishing attacks, typo squatting, and brand impersonation. It's a simple Python script you can run from the command line to find those lookalike domains where adversaries might try to attack you.
Key Features of dnstwist
Before we dive into the practical examples, let's explore some of the standout features that make dnstwist such a powerful tool:
- HTML Similarity and Fuzzy Hashing: dnstwist can compare the HTML code of two websites using fuzzy hashing techniques. This capability helps identify instances where an attacker may have cloned a portion of your website and modified it for a watering hole attack or credential harvesting scam.
- Automatic Website Screenshots: One of the coolest features of dnstwist is its ability to automatically capture screenshots of the websites it finds during its scans. This visual representation can be invaluable for analysts trying to quickly assess the nature and intent of a suspicious domain.
- Phishing Detection: dnstwist includes specialized functionality for phishing detection, leveraging techniques like fuzzy hashing and HTML similarity comparisons to identify potential phishing sites.
- Python API: Being a Python script, dnstwist can be imported and used as part of your own code, making it a versatile addition to your cybersecurity toolkit.
- Extensive Permutation Techniques: dnstwist employs a wide range of permutation techniques to generate potential lookalike domains, including character substitution, addition, removal, and even Unicode representation.
With such a powerful feature set, dnstwist becomes an invaluable asset for cybersecurity professionals, researchers, and anyone concerned about protecting their online presence from typo squatting and brand impersonation attacks.
Checking for Lookalikes with DNSTwist
Let's start by checking out the online, browser-based version of DNSTwist at https://dnstwist.it.
Here you can enter a domain name like youtube.com and have DNSTwist scan for strange permutations, looking for DNS records to see if those domains actually exist somewhere on the internet.
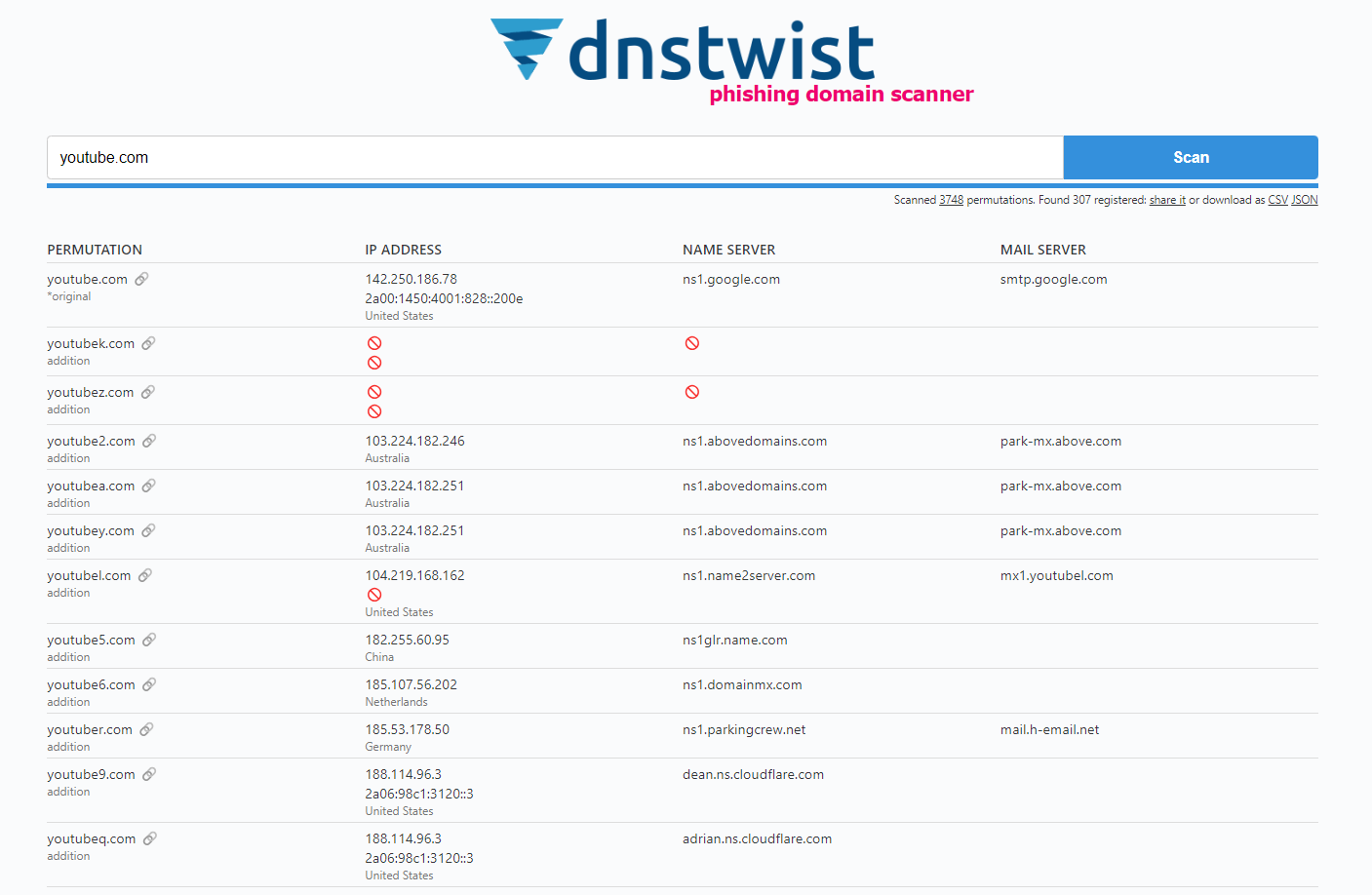
Scanning for youtube.com reveals dozens, if not hundreds, of potential typo squatting domains – everything from youjtube.com and yotubue.com (simple misspellings) to yoiutube.com (mixed up letters) to yu0tube.com (homoglyphs substituting similar-looking characters). The results even include wandering extensions like youtube.net, youtube.org, and others. I have discussed lookalike domains in a previous blog post that you can check out here:

Many of these are likely owned by YouTube themselves as a defensive measure against typo squatting. But plenty look...suspicious. Domains like yoitube.com, ytubevids.xyz, and yotube.com.ai are matches that could easily trick someone into visiting, especially if deployed as part of a phishing campaign.
The browser tool gives you the bare domain details – registrant, DNS records, etc. But DNSTwist's real power comes when you run the Python script locally and take advantage of advanced functionality like fuzzy hash HTML comparison to detect cloned sites and automatic website screenshots.
Installing and Running DNSTwist
You can install DNStwist on any server, really, as log as it has python on it. However, to prevent network bottlenecks or potential blocking of some of the domains by your network provider, you can run it on a server in the cloud> There are several cloud providers out there but feel free to choose one of your liking. You can use the links below to get free trials on any of the cloud providers.
- Vultr - Get 100 USD in credits to try out in 30 days. Vultr also offers Windows Server VPSs at a cheaper cost and has tones of other operating systems to choose from as compared to Linode and Digital Ocean
- Digital Ocean - Get 200 USD in credits to try out in 60 days!
- Linode - Get 100 USD in credits to try out in 60 days!
- Microsoft Azure
- AWS
- Google Cloud Platform
To see DNSTwist in action, I'll install and run it from a cloud server on Digital Ocean. This prevents my home network from blocking any of the detected domains due to their potentially malicious nature.
After creating a new Digital Ocean droplet (virtual machine) and logging in via SSH, I install Python 3, pip (Python's package installer), and virtualenv to create an isolated Python environment:
sudo apt install python3 python3-pip
sudo pip3 install virtualenv
virtualenv env
source env/bin/activate
With the virtualenv activated, I can pip install dnstwist:
pip install dnstwist
For other distributions, you can install DNStwist using the following instructions:
Python PIP
pip install dnstwist[full]
Alternatively install the bare minimum and add other requirements manually depending on your needs:
pip install dnstwist
Git
If you want to run the latest version of the code, you can install it from Git:
git clone https://github.com/elceef/dnstwist.git
cd dnstwist
pip install .
Debian/Ubuntu/Kali Linux
Invoke the following command to install the tool with all extra packages:
sudo apt install dnstwist
Fedora Linux
sudo dnf install dnstwist
macOS
This will install dnstwist along with all dependencies, and the binary will be added to $PATH.
brew install dnstwist
Docker
Pull and run official image from the Docker Hub:
docker run -it elceef/dnstwist
Alternatively, you can build your local images:
docker build -t dnstwist .
docker build -t dnstwist:phash --build-arg phash=1 .
Running dnstwist
DNS twist offers a tonne of options when running on the terminal which you can view by running dnstwist -h
Let us try finding some of the domains that might be used to trick users trying to get to facebook.com.
dnstwist -r facebook.com
The -r flag tells DNSTwist to only show registered domains rather than every possible permutation. After about a minute, it spits out a long list of results like, fbacebook.com, facebokook.com, and many more. Some are obvious typos, while others substitute similar-looking characters like the digit 0 for o or use funky new top-level domains like .xyz.
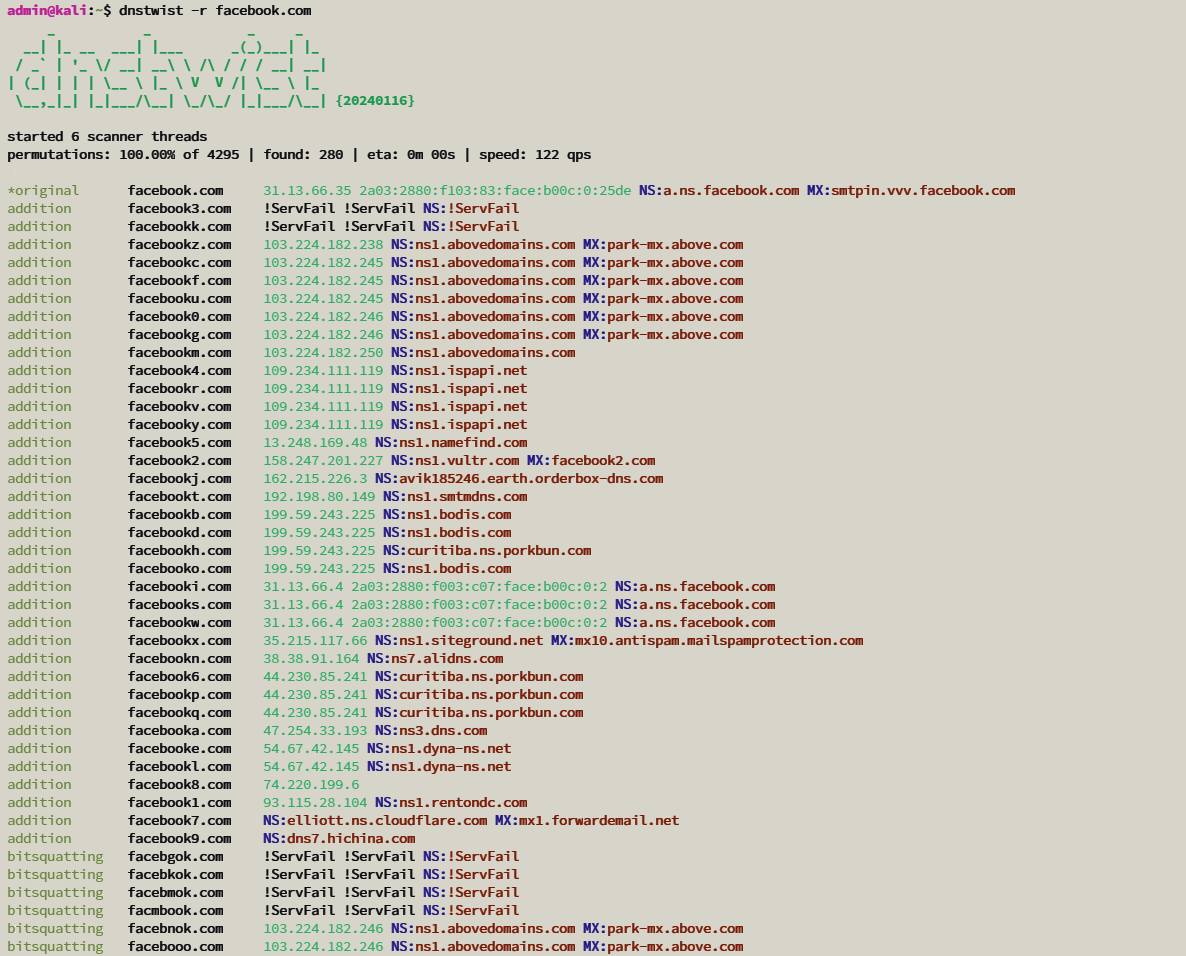
Many major websites and brands defensively register common typo squatting domains precisely to prevent their use in attacks. So plenty of matches may be legitimate, registered properties. But plenty of others could represent a threat.
Finding Malicious Lookalikes for Top Sites
To make it interesting, we can try digging into the top sites to see what comes up.
mkdir google
dnstwist -r --screenshots=google --phash google.com
The --screenshots flag tells DNSTwist to navigate to each registered domain it finds and capture a screenshot, saving them in the google/ folder specified. The --phash flag enables perceptual hashing, which can detect similar-looking phishing pages by hashing and comparing visual aspects of the website code and rendering.
DNSTwist gets to work, rapidly firing through permutations of google.com and downloading screenshots of any registered domains it encounters that respond with website content.
After clustering the visual matches, we get a treasure trove of interesting results in the google/ folder:
- Lots of cheap domain registrations offering the names for sale
- Some rather embarrassingly amateur-looking phishing pages
- A few that seem to be genuinely attempting to imitate the real Google experience, including Google Translate, the Play Store, and Google's actual properties (which they likely own defensively)
DNSTwist provides an incredibly rich data set for analysts to dig through potential phishing, malware, and social engineering threats -- both those explicitly targeting a brand and those capitalizing on typos more generally. Pair it with other threat intelligence tools, and you have a potent way to get ahead of attacks.
Checking for Threats to Your Own Domains
You can also run DNSTwist scan to check for any suspicious typo squatting of on your personal and business domains
dnstwist -r franklinetech.com
Security researchers can also use dnstwist to come up with domains of testing their company/clients preparedness against such.
We have only scratched the surface of what dnstwist can do. Be sure to check out their GitHub repo for full details.



